Security News

A Syslog server will only collect messages in the Syslog format but it is possible to change other formats into the Syslog layout before sending them to a Syslog server; this is called "Conversion." The other option is to set up a non-specific TFTP server and implement format conversion through a post-receipt process; this is called "Consolidation." If you don't convert either before or after the transfer, you will be storing raw log messages. If you receive log messages through a Syslog server, they will be written either to files or to a database in the Syslog format.

Leicester City Council continues to battle a suspected ransomware attack while keeping schtum about the key details. The Register has repeatedly asked for a confirmation or denial of ransomware's involvement from the council, but after ignoring us for ten days it finally replied today, only to say it still couldn't share anything beyond official statements.
In today's digital-first business environment dominated by SaaS applications, organizations increasingly depend on third-party vendors for essential cloud services and software solutions. As more...

Network monitoring tools provide automated network discovery and often also draw up network topology maps. Network device monitoring is often also referred to as network performance monitoring.

When tech billionaires and corporations steer AI, we get AI that tends to reflect the interests of tech billionaires and corporations, instead of the public. To benefit society as a whole we need an AI public option-not to replace corporate AI but to serve as a counterbalance-as well as stronger democratic institutions to govern all of AI. Like public roads and the federal postal system, a public AI option could guarantee universal access to this transformative technology and set an implicit standard that private services must surpass to compete.
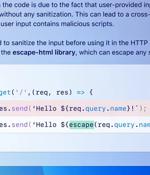
GitHub on Wednesday announced that it's making available a feature called code scanning autofix in public beta for all Advanced Security customers to provide targeted recommendations in an effort...

ManageEngine RMM Central: This software package provides system discovery and documentation, automated monitoring, patch management, remote control, and mobile device management for use by managed service providers. RMM software makes a huge difference in the field of system support.

Attackers are exploiting the recently patched JetBrains TeamCity auth bypass vulnerability to deliver ransomware, cryptominers and remote access trojans, according to Trend Micro researchers. CVE-2024-27198, an authentication bypass vulnerability affecting the TeamCity server, has been disclosed and fixed in early March, along with CVE-2024-27199 - a directory traversal vulnerability in the same instance.

When you read reports about cyber-attacks affecting operational technology (OT), it’s easy to get caught up in the hype and assume every single one is sophisticated. But are OT environments all...

The U.S. Treasury Department's Office of Foreign Assets Control (OFAC) on Wednesday announced sanctions against two 46-year-old Russian nationals and the respective companies they own for engaging...