Security News

The North Korea-linked threat actor known as Kimsuky has been linked to a new set of attacks targeting university staff, researchers, and professors for intelligence gathering purposes. Kimsuky, also known by the names APT43, ARCHIPELAGO, Black Banshee, Emerald Sleet, Springtail, and Velvet Chollima, is just one of the myriad offensive cyber teams operating under the direction of the North Korean government and military.
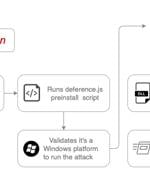
The North Korea-linked threat actor known as Moonstone Sleet has continued to push malicious npm packages to the JavaScript package registry with the aim of infecting Windows systems, underscoring the persistent nature of their campaigns. The security arm of the cloud monitoring firm is tracking the threat actor under the name Stressed Pungsan, which exhibits overlaps with a newly discovered North Korean malicious activity cluster dubbed Moonstone Sleet.

South Korea's National Cyber Security Center (NCSC) warns that state-backed DPRK hackers hijacked flaws in a VPN's software update to deploy malware and breach networks. [...]

The U.S. Department of Justice on Thursday unsealed an indictment against a North Korean military intelligence operative for allegedly carrying out ransomware attacks against healthcare facilities in the country and funneling the payments to orchestrate additional intrusions into defense, technology, and government entities across the world. "Rim Jong Hyok and his co-conspirators deployed ransomware to extort U.S. hospitals and health care companies, then laundered the proceeds to help fund North Korea's illicit activities," said Paul Abbate, deputy director of the Federal Bureau of Investigation.

The US Department of Justice on Thursday charged a North Korean national over a series of ransomware attacks on stateside hospitals and healthcare providers, US defense companies, NASA, and even a Chinese target. An indictment [PDF] named Rim Jong Hyok as a participant in "a conspiracy to hack and extort US hospitals and other health care providers, launder the ransom proceeds, and then use these proceeds to fund additional computer intrusions into defense, technology, and government entities worldwide."

A North Korea-linked threat actor known for its cyber espionage operations has gradually expanded into financially-motivated attacks that involve the deployment of ransomware, setting it apart from other nation-state hacking groups linked to the country. "APT45 is a long-running, moderately sophisticated North Korean cyber operator that has carried out espionage campaigns as early as 2009," researchers Taylor Long, Jeff Johnson, Alice Revelli, Fred Plan, and Michael Barnhart said.

American cybersecurity company KnowBe4 says a person it recently hired as a Principal Software Engineer turned out to be a North Korean state actor who attempted to install information-stealing on its devices. Before hiring the threat actor, KnowBe4 performed background checks, verified the provided references, and conducted four video interviews to ensure they were a real person and that his face matched the one on his CV. However, it was later determined that the person had submitted a U.S. person's stolen identity to dodge the preliminary checks, and also used AI tools to create a profile picture and match that face during the video conference calls.

If it can happen to folks that run social engineering defence training, what hope for the rest of us? Security awareness and training provider KnowBe4 hired a fake North Korean IT worker for a...

BeaverTail refers to a JavaScript stealer malware that was first documented by Palo Alto Networks Unit 42 in November 2023 as part of a campaign dubbed Contagious Interview that aims to infect software developers with malware through a supposed job interview process. Securonix is tracking the same activity under the moniker DEV#POPPER. Besides siphoning sensitive information from web browsers and crypto wallets, the malware is capable of delivering additional payloads like InvisibleFerret, a Python backdoor that's responsible for downloading AnyDesk for persistent remote access.

Japan's Computer Emergency Response Team Coordination Center is warning that Japanese organizations are being targeted in attacks by the North Korean 'Kimsuky' threat actors. The US government has attributed Kimsuky as a North Korean advanced persistent threat group that conducts attacks against targets worldwide to gather intelligence on topics of interest to the North Korean government.