Security News

The popular Zero2Automated malware analysis and reverse-engineering course has a Black Friday 2023 through Cyber Monday sale, where you can get 25% off sitewide, including gift certificates and courses. Started in May 2020 by two well-known reverse engineers, Vitali Kremez and Daniel Bunce, Zero2Automated is more than just an online training course.

Delivery- and shipping-themed email messages are being used to deliver a sophisticated malware loader known as WailingCrab. "The malware itself is split into multiple components, including a...

Akamai has uncovered two zero-day bugs capable of remote code execution, both being exploited to distribute the Mirai malware and built a botnet army for distributed denial of service attacks. Because the security holes aren't plugged yet, Akamai's Security Intelligence Response Team did not name the brands or the affected devices.

Atomic Stealer Sends Macs Malware Through False Browser DownloadsTechRepublicToggle TechRepublic mobile menuTechRepublic PremiumTechRepublic close modalTechRepublic close modalTechRepublic close modalTechRepublicTechRepublic on TwitterTechRepublic on FacebookTechRepublic on LinkedInTechRepublic on FlipboardLoadingLoadingLoadingLoadingLoading. Anti-malware software provider Malwarebytes has described a new variant of Atomic Stealer, which is malware targeting Apple users.

A new Mirai-based malware botnet named 'InfectedSlurs' has been exploiting two zero-day remote code execution vulnerabilities to infect routers and video recorder devices. The malware hijacks the devices to make them part of its DDoS swarm, presumably rented for profit.
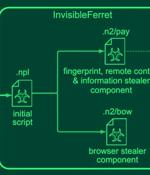
North Korean threat actors have been linked to two campaigns in which they masquerade as both job recruiters and seekers to distribute malware and obtain unauthorized employment with organizations...

The Lumma information-stealer malware is promoting a new feature that allegedly allows cybercriminals to restore expired Google cookies, which can be used to hijack Google accounts. Session cookies are specific web cookies used to allow a browsing session to log in to a website's services automatically.

The Lumma information-stealer malware is promoting a new feature that allegedly allows cybercriminals to restore expired Google cookies, which can be used to hijack Google accounts. Restoring these cookies would allow Lumma operators to gain unauthorized access to any Google account even after the legitimate owner has logged out of their account or their session has expired.

A sophisticated phishing campaign pushing the DarkGate malware infections has recently added the PikaBot malware into the mix, making it the most advanced phishing campaign since the Qakbot operation was dismantled. In a new report by Cofense, researchers explain that the DarkGate and Pikabot campaigns use tactics and techniques similar to previous Qakbot campaigns, indicating that the Qbot threat actors have now moved on to the newer malware botnets.

A new variant of the Agent Tesla malware has been observed delivered via a lure file with the ZPAQ compression format to harvest data from several email clients and nearly 40 web browsers. "ZPAQ...