Security News
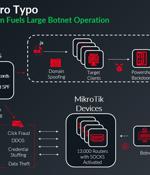
A global network of about 13,000 hijacked Mikrotik routers has been employed as a botnet to propagate malware via spam campaigns, the latest addition to a list of botnets powered by MikroTik...

Cybersecurity researchers have found that bad actors are continuing to have success by spoofing sender email addresses as part of various malspam campaigns. Faking the sender address of an email...

The notorious Emotet malware has returned with renewed vigor as part of a high-volume malspam campaign designed to drop payloads like IcedID and Bumblebee. "Hundreds of thousands of emails per day" have been sent since early November 2022, enterprise security company Proofpoint said last week, adding, "The new activity suggests Emotet is returning to its full functionality acting as a delivery network for major malware families."

A malspam campaign has been found distributing the new META malware, a new info-stealer malware that appears to be rising in popularity among cybercriminals. META is one of the novel info-stealers, along with Mars Stealer and BlackGuard, whose operators wish to take advantage of Raccoon Stealer's exit from the market that left many searching for their next platform.

SquirrelWaffle, a new malware loader, is mal-spamming malicious Microsoft Office documents to deliver Qakbot malware and the penetration-testing tool Cobalt Strike - two of the most common threats regularly observed targeting organizations around the world. Cisco Talos researchers said on Tuesday that they got wind of the malspam campaigns beginning in mid-September, when they saw the boobytrapped Office documents working to infect systems with SquirrelWaffle in the initial stage of the infection chain.

In one case, the tango seems to be with QBot and IcedID, two banking trojans that are often seen delivering various ransomware strains as the final payload in the attack. Return to initial payload. Earlier this year, researchers observed a malicious email campaign spreading weaponized Office documents that delivered QBot trojan, only to change the payload after a short while.

Threat actors have taken advantage of the ongoing uncertainty around the 2020 U.S. election to unleash a new malspam campaign aimed at spreading the Qbot trojan. Criminals behind Qbot resurfaced the day after the election with a wave of spam emails that attempt to lure victims with messages claiming to have information about election interference, according to new researchers.

"The new campaign sports longtime Emotet tactics: emails carrying links or documents w/ highly obfuscated malicious macros that run a PowerShell script to download the payload from 5 download links," according to Microsoft Security Intelligence researchers on Twitter. The spam emails contain either a URL or an attachment, and purport to be sending a document in reply to existing email threads - a known trick of Emotet.

A large U.S. manufacturing company is the latest organization to be targeted with the LokiBot trojan - although this most recent campaign harbored some bizarre red flags.
