Security News

A new information stealer malware named 'MetaStealer' has appeared in the wild, stealing a wide variety of sensitive information from Intel-based macOS computers. Although the malware has some similarities with Atomic Stealer, another Go-based macOS targeting info-stealer, the code overlap is limited, and the delivery methods are different.
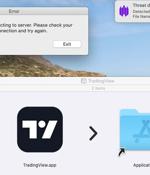
A new information stealer malware called MetaStealer has set its sights on Apple macOS, making the latest in a growing list of stealer families focused on the operating system after Stealer, Pureland, Atomic Stealer, and Realst. "Threat actors are proactively targeting macOS businesses by posing as fake clients in order to socially engineer victims into launching malicious payloads," SentinelOne security researcher Phil Stokes said in a Monday analysis.
A new malvertising campaign has been observed distributing an updated version of a macOS stealer malware called Atomic Stealer, indicating that it's being actively maintained by its author. An off-the-shelf Golang malware available for $1,000 per month, Atomic Stealer first came to light in April 2023.

A newer version of the Atomic Stealer macOS malware has a new trick that allows it to bypass the operating system's Gatekeeper, Malwarebytes researchers have discovered. "Criminals who buy the toolkit have been distributing it mostly via cracked software downloads but are also impersonating legitimate websites and using ads on search engines such as Google to lure victims in," says Malwarebytes researcher Jérôme Segura.

A new variant of malware called XLoader is targeting macOS users. A new report from cybersecurity company SentinelOne shows how the XLoader malware evolved.

A new macOS-specific variant of the well known XLoader malware is being delivered disguised as the "OfficeNote" app. XLoader is a malware-as-a-service infostealer and botnet that has been active since 2015, but first appeared as a macOS variant in 2021, written in Java.
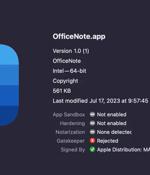
A new variant of an Apple macOS malware called XLoader has surfaced in the wild, masquerading its malicious features under the guise of an office productivity app called "OfficeNote." "The new version of XLoader is bundled inside a standard Apple disk image with the name OfficeNote.dmg," SentinelOne security researchers Dinesh Devadoss and Phil Stokes said in a Monday analysis.
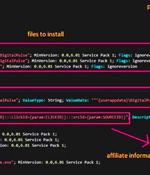
Threat actors are leveraging access to malware-infected Windows and macOS machines to deliver a proxy server application and use them as exit nodes to reroute proxy requests. According to AT&T Alien Labs, the unnamed company that offers the proxy service operates more than 400,000 proxy exit nodes, although it's not immediately clear how many of them were co-opted by malware installed on infected machines without user knowledge and interaction.
A new malware family called Realst has become the latest to target Apple macOS systems, with a third of the samples already designed to infect macOS 14 Sonoma, the upcoming major release of the operating system. Written in the Rust programming language, the malware is distributed in the form of bogus blockchain games and is capable of "Emptying crypto wallets and stealing stored password and browser data" from both Windows and macOS machines.

A new Mac malware named "Realst" is being used in a massive campaign targeting Apple computers, with some of its latest variants including support for macOS 14 Sonoma, which is still in development. In reality, the game installers infect devices with information-stealing malware, such as RedLine Stealer on Windows and Realst on macOS. This type of malware will steal data from the victim's web browsers and cryptocurrency wallet apps and send them back to the threat actors.