Security News
Cybersecurity researchers have disclosed that the LightSpy spyware allegedly targeting Apple iOS users is in fact a previously undocumented macOS variant of the implant. The findings come from...

A macOS version of the LightSpy surveillance framework has been discovered, confirming the extensive reach of a tool only previously known for targeting Android and iOS devices. LightSpy is a modular iOS and Android surveillance framework used to steal a wide variety of data from people's mobile devices, including files, screenshots, location data, voice recordings during WeChat calls, and payment information from WeChat Pay, and data exfiltration from Telegram and QQ Messenger.

Cybersecurity researchers have discovered a new information stealer targeting Apple macOS systems that's designed to set up persistence on the infected hosts and act as a spyware. Dubbed Cuckoo by...

Malicious ads and bogus websites are acting as a conduit to deliver two different stealer malware, including Atomic Stealer, targeting Apple macOS users. The ongoing infostealer attacks targeting...

Oracle warned Apple customers to delay installing the latest macOS 14.4 Sonoma update because it will break Java on ARM-based Macs. According to Garcia-Ribeyro, since the Java Virtual Machine uses dynamic code generation and accesses memory in protected memory regions to ensure correctness and performance, its process will be terminated after deploying the macOS 14.4 update.

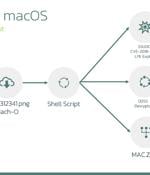
Several companies operating in the cryptocurrency sector are the target of a newly discovered Apple macOS backdoor codenamed RustDoor. RustDoor was first documented by Bitdefender last week,...

Apple macOS users are the target of a new Rust-based backdoor that has been operating under the radar since November 2023.The backdoor codenamed “RustDoor” by Bitdefender, has been found to impersonate an update for Microsoft Visual Studio and target both Intel and Arm architectures.

A new Rust-based macOS malware spreading as a Visual Studio update to provide backdoor access to compromised systems uses infrastructure linked to the infamous ALPHV/BlackCat ransomware gang. Written in Rust, the malware can run on Intel-based and ARM architectures, say researchers at cybersecurity company Bitdefender, who are tracking it as RustDoor.

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Wednesday added a high-severity flaw impacting iOS, iPadOS, macOS, tvOS, and watchOS to its Known Exploited Vulnerabilities...

Cracked software have been observed infecting Apple macOS users with a previously undocumented stealer malware capable of harvesting system information and cryptocurrency wallet data. Kaspersky,...