Security News

A new watering hole attack has been discovered targeting macOS users and visitors of a pro-democracy radio station website in Hong Kong and infecting them with the DazzleSpy malware. Watering hole attacks involve the infection of a legitimate website with malware, targeting the demographic of that site, and in some cases, only specific IP addresses.
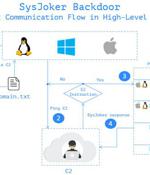
A new cross-platform backdoor called "SysJoker" has been observed targeting machines running Windows, Linux, and macOS operating systems as part of an ongoing espionage campaign that's believed to have been initiated during the second half of 2021. "SysJoker masquerades as a system update and generates its by decoding a string retrieved from a text file hosted on Google Drive," Intezer researchers Avigayil Mechtinger, Ryan Robinson, and Nicole Fishbein noted in a technical write-up publicizing their findings.

Microsoft is now rolling out redesigned hardware indicator flyouts that align with Windows 11's design to all Windows Insiders in the Dev Channel. "We have updated the flyout design for the hardware indicators for brightness, volume, camera privacy, camera on/off and airplane mode, to align with Windows 11 design principles," Microsoft's Amanda Langowski and Brandon LeBlanc said.

Microsoft on Monday released details about a bug in macOS that Apple fixed last month - named "Powerdir" - that could let attackers hijack apps, install their own nasty apps, use the microphone to eavesdrop or grab screenshots of whatever's displayed on your screen. Introduced in 2012 in macOS Mountain Lion, TCC helps users to configure their apps' privacy settings by requiring that all apps get user consent before accessing files in Documents, Downloads, Desktop, iCloud Drive, calendar and network volumes, as well as before the apps are allowed to access the device's camera, microphone or location.

During this year's first Patch Tuesday, Microsoft has addressed a critical severity Office vulnerability that can let attackers execute malicious code remotely on vulnerable systems. The security flaw, tracked as CVE-2022-21840, is a remote code execution bug that attackers can exploit with no privileges on the targeted devices as part of low complexity attacks that require user interaction.

A new multi-platform backdoor malware named 'SysJoker' has emerged in the wild, targeting Windows, Linux, and macOS with the ability to evade detection on all three operating systems. The discovery of the new malware comes from researchers at Intezer who first saw signs of its activity in December 2021 after investigating an attack on a Linux-based web server.

A new multi-platform backdoor malware named 'SysJocker' has emerged in the wild, targeting Windows, Linux, and macOS with the ability to evade detection on all three operating systems. The discovery of the new malware comes from researchers at Intezer who first saw signs of its activity in December 2021 after investigating an attack on a Linux-based web server.

Dubbed SysJoker by Intezer, the backdoor is used for establishing initial access on a target machine. A possible attack vector for SysJoker is an infected npm package, according to Intezer's analysis - an increasingly popular vector for dropping malware on targets.
Microsoft on Monday disclosed details of a recently patched security vulnerability in Apple's macOS operating system that could be weaponized by a threat actor to expose users' personal information. Tracked as CVE-2021-30970, the flaw concerns a logic issue in the Transparency, Consent and Control security framework, which enables users to configure the privacy settings of their apps and provide access to protected files and app data.

Microsoft says threat actors could use a macOS vulnerability to bypass Transparency, Consent, and Control technology to access users' protected data. The Microsoft 365 Defender Research Team has reported the vulnerability dubbed powerdir to Apple on July 15, 2021, via the Microsoft Security Vulnerability Research.