Security News

LockBit ransomware developers were secretly building a new version of their file encrypting malware, dubbed LockBit-NG-Dev - likely to become LockBit 4.0, when law enforcement took down the cybercriminal's infrastructure earlier this week. While previous LockBit malware is built in C/C++, the latest sample is a work-in-progress written in.

The U.S. State Department has announced monetary rewards of up to $15 million for information that could lead to the identification of key leaders within the LockBit ransomware group and the...

The U.S. State Department is now also offering rewards of up to $15 million to anyone who can provide information about LockBit ransomware gang members and their associates. 10 million is offered for information that could lead to locating or identifying LockBit leadership, and an extra $5 million is available for tips that could lead to the apprehension of LockBit ransomware affiliates.

The latest revelation from law enforcement authorities in relation to this week's LockBit leaks is that the ransomware group had registered nearly 200 "Affiliates" over the past two years. List of LockBit 3.0 affiliates published by the NCA. The FBI first started investigating LockBit in 2020, and the group has since developed new variants of its ransomware, the latest of which was released in mid-2022, so the data shared today likely shows all the affiliates that have ever deployed the most recent version of LockBit.
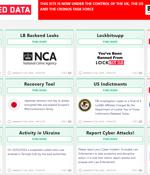
After the infosec world was invigorated by the announcement of LockBit's site being seized yesterday, the authorities involved in the takedown operation - dubbed "Operation Cronos" - have now completely taken over the group's leak site and turned it into an exposé hub. In typical LockBit style, its countdown timers have been hijacked to reveal the times at which various pieces of information will be revealed, including what appears to be the identity of LockBit's leader.

The U.K. National Crime Agency (NCA) on Tuesday confirmed that it obtained LockBit's source code as well as intelligence pertaining to its activities and their affiliates as part of a dedicated...

In the wake of yesterday's surprise law enforcement takeover of LockBit's leak site, the UK National Crime Agency and Europol have shared more information about the extent of the takedown. "Today, after infiltrating the group's network, the NCA has taken control of the infrastructure that allows the Lockbit service to operate, compromising their entire criminal enterprise and damaging their credibility," the Agency said.

Law enforcement arrested two operators of the LockBit ransomware gang in Poland and Ukraine, created a decryption tool to recover encrypted files for free, and seized over 200 crypto-wallets after hacking the cybercrime gang's servers in an international crackdown operation. The global LockBit crackdown was coordinated by Operation Cronos, a task force headed by the U.K. National Crime Agency and coordinated in Europe by Europol and Eurojust.

Law enforcement arrested two operators of the LockBit ransomware gang in Poland and Ukraine, created a decryption tool to recover encrypted files for free, and seized over 200 crypto-wallets after hacking the cybercrime gang's servers in an international crackdown operation. The global LockBit crackdown was coordinated by Operation Cronos, a task force headed by the U.K. National Crime Agency and coordinated in Europe by Europol and Eurojust.

On Monday afternoon, LockBit's leak site has been taken over by a coalition of law enforcement agencies and is showing a seizure notice that promises more details today, at 11:30 GMT. "This site is now under the control of The National Crime Agency of the UK, working in close cooperation with the FBI and the international law enforcement task force, 'Operation Cronos'," the notice says. "We can confirm that Lockbit's services have been disrupted as a result of International Law Enforcement action - this is an ongoing and developing operation."