Security News > 2024 > February > Cops turn LockBit ransomware gang's countdown timers against them
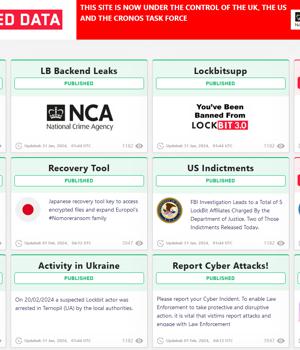
After the infosec world was invigorated by the announcement of LockBit's site being seized yesterday, the authorities involved in the takedown operation - dubbed "Operation Cronos" - have now completely taken over the group's leak site and turned it into an exposé hub.
In typical LockBit style, its countdown timers have been hijacked to reveal the times at which various pieces of information will be revealed, including what appears to be the identity of LockBit's leader.
The US Department of Justice also unsealed an indictment today charging Russian nationals Artur Sungatov and Ivan Kondratyev with deploying LockBit ransomware against US victims.
According to alleged messages exchanged between LockBit and malware collectors vx-underground, LockBit believes only servers running PHP elements were impacted and that its backups were untouched, which could mean a recovery is on the cards.
"LockBit themselves are claiming that only servers running PHP elements were impacted, data is safe, and backup servers were unaffected which, if true, will probably mean Lockbit can recover fairly swiftly."
Given the degree to which we can already see the NCA taking over LockBit's site, West at WithSecure said perhaps a more likely scenario is one where LockBit is unaware of the extent to which it's been compromised and won't ever recover.
News URL
https://go.theregister.com/feed/www.theregister.com/2024/02/20/nca_lockbit_takedown/