Security News

A vulnerability in the GNU C Library can be exploited by attackers to gain root privileges on many popular Linux distributions, according to Qualys researchers. Dubbed "Looney Tunables", CVE-2023-4911 is a buffer overflow vulnerability in the dynamic loader's processing of the GLIBC TUNABLES environment variable.

The flaw, dubbed Looney Tunables, arises from the GNU C Library's dynamic loader mishandling of the GLIBC TUNABLES environmental variable. Because GNU C Library, commonly known as glibc, is found in most Linux systems, this is something of an issue.

A new Linux security vulnerability dubbed Looney Tunables has been discovered in the GNU C library's ld.so dynamic loader that, if successfully exploited, could lead to a local privilege...

A new Linux vulnerability known as 'Looney Tunables' enables local attackers to gain root privileges by exploiting a buffer overflow weakness in the GNU C Library's ld. The GNU C Library is the GNU system's C library and is in most Linux kernel-based systems.

The developers of Free Download Manager have published a script to check if a Linux device was infected through a recently reported supply chain attack. Free Download Manager is a popular cross-platform download manager that offers torrenting, proxying, and online video downloads through a user-friendly interface.

The China-linked threat actor known as Earth Lusca has been observed targeting government entities using a never-before-seen Linux backdoor called SprySOCKS. Earth Lusca was first documented by Trend Micro in January 2022, detailing the adversary's attacks against public and private sector entities across Asia, Australia, Europe, North America. Active since 2021, the group has relied on spear-phishing and watering hole attacks to pull off its cyber espionage schemes.

Microsoft has released Windows Subsystem for Linux 2.0.0 with a set of new opt-in experimental features, including a new network mode and automated memory and disk size cleanup. This WSL update introduces "Mirrored mode networking," a new networking mode that not only brings new capabilities but also enhances network compatibility.

A Chinese espionage-focused hacker tracked as 'Earth Lusca' was observed targeting government agencies in multiple countries, using a new Linux backdoor dubbed 'SprySOCKS.'. Trend Micro's analysis of the novel backdoor showed that it originates from the Trochilus open-source Windows malware, with many of its functions ported to work on Linux systems.
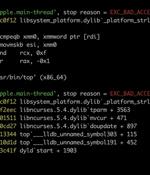
A set of memory corruption flaws have been discovered in the ncurses programming library that could be exploited by threat actors to run malicious code on vulnerable Linux and macOS systems. "Using environment variable poisoning, attackers could chain these vulnerabilities to elevate privileges and run code in the targeted program's context or perform other malicious actions," Microsoft Threat Intelligence researchers Jonathan Bar Or, Emanuele Cozzi, and Michael Pearse said in a technical report published today.
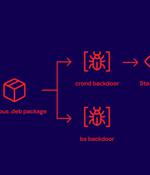
A download manager site served Linux users malware that stealthily stole passwords and other sensitive information for more than three years as part of a supply chain attack. The modus operandi entailed establishing a reverse shell to an actor-controlled server and installing a Bash stealer on the compromised system.