Security News

Threat actors have revived an old and relatively inactive ransomware family known as TellYouThePass, deploying it in attacks against Windows and Linux devices targeting a critical remote code execution bug in the Apache Log4j library. KnownSec 404 Team's Heige first reported these attacks on Twitter on Monday after observing that the ransomware was dropped on old Windows systems using exploits targeting the flaw tracked as CVE-2021-44228 and known as Log4Shell.

For anyone looking to gain an extra layer of privacy on a desktop or laptop, Kodachi Linux might be the perfect option. Do you veer toward the over-cautious when it comes to your privacy? Do you loathe the idea that you're being tracked by third-party cookies, and standard browsers and operating systems aren't capable of doing enough to keep you safe? At the same time, are you too busy to learn a new operating system?

Here's a single command you can run to test and see if you have any vulnerable packages installed. Are you using it as part of a Java project, is it rolled into a container, did you install it with your distribution package manager, and which log4j packages did you install? Or did you install it from source? Because of this, you might not even know if your server is vulnerable.

Critical RCE 0day in Apache Log4j library exploited in the wildA critical zero-day vulnerability in Apache Log4j, a widely used Java logging library, is being leveraged by attackers in the wild.Kali Linux 2021.4 released: Wider Samba compatibility, The Social-Engineer Toolkit, new tools, and more!Offensive Security released Kali Linux 2021.4, which comes with a number of improvements: wider Samba compatibility, switching package manager mirrors, enhanced Apple M1 support, Kaboxer theming, updates to Xfce, GNOME and KDE, Raspberry Pi Zero 2 W + USBArmory MkII ARM images, as well as new tools.

Kali Linux 2021.4 was released today by Offensive Security and includes further Apple M1 support, increased Samba compatibility, nine new tools, and an update for all three main desktop. Kali Linux is a Linux distribution allowing cybersecurity professionals and ethical hackers to perform penetration testing and security audits against internal and remote networks.

Need to lock down that Linux server so certain remote users can only access a specific directory and only for file upload and download purposes? Jack Wallen shows you how. When you have a server with SSH access, unless you've configured it otherwise, any user with an account on that system can log in and, if they have the permissions and skill, wreak havoc on your server.

Offensive Security released Kali Linux 2021.4, which comes with a number of improvements: wider Samba compatibility, switching package manager mirrors, enhanced Apple M1 support, Kaboxer theming, updates to Xfce, GNOME and KDE, Raspberry Pi Zero 2 W + USBArmory MkII ARM images, as well as new tools. Starting Kali Linux 2021.4, the Samba client is now configured for Wide Compatibility so that it can connect to pretty much every Samba server out there, regardless of the version of the protocol in use.
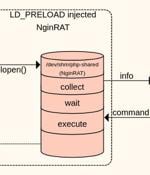
E-commerce platforms in the U.S., Germany, and France have come under attack from a new form of malware that targets Nginx servers in an attempt to masquerade its presence and slip past detection by security solutions. "This novel code injects itself into a host Nginx application and is nearly invisible," Sansec Threat Research team said in a new report.

Researchers have unearthed a new remote access trojan for Linux that employs a never-before-seen stealth technique that involves masking its malicious actions by scheduling them for execution on February 31st, a non-existent calendar day. Dubbed CronRAT, the sneaky malware "Enables server-side Magecart data theft which bypasses browser-based security solutions," Sansec Threat Research said.

Security researchers have discovered a new remote access trojan for Linux that keeps an almost invisible profile by hiding in tasks scheduled for execution on a non-existent day, February 31st. Dubbed CronRAT, the malware is currently targeting web stores and enables attackers to steal credit card data by deploying online payment skimmers on Linux servers. CronRAT abuses the Linux task scheduling system, cron, which allows scheduling tasks to run on non-existent days of the calendar, such as February 31st. The Linux cron system accepts date specifications as long as they have a valid format, even if the day does not exist in the calendar - which means that the scheduled task won't execute.