Security News

Why? GitLab explained: "Due to Microsoft Windows' dominance in desktop operating systems, Windows is the platform most targeted by spyware, viruses, and ransomware." Windows' security mess has never been just because Windows is more popular.

Offensive Security has released Kali Linux 2022.3, the third version of 2022, with virtual machine improvements, Linux Kernel 5.18.5, new tools to play with, and improved ARM support. With this release, Kali Linux is using Linux Kernel 5.18.5.

Offensive Security has released Kali Linux 2022.3, the third version of 2022, with virtual machine improvements, Linux Kernel 5.18.5, new tools to play with, and improved ARM support. With this release, Kali Linux is using Linux Kernel 5.18.5.

Offensive Security has released Kali Linux 2022.3, the latest version of its popular penetration testing and digital forensics platform. The Kali Team knows the importance of practicing instead of relying on theory, and for infosecurity professionals, test labs are a way to test tools and hone their own skills in a legal environment.
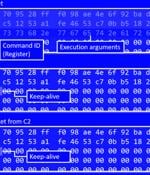
"This family borrows heavily from the original Mirai source code, but what separates it from other IoT malware families is its built-in capability to brute force credentials and gain access to SSH servers instead of Telnet as implemented in Mirai," Fortinet FortiGuard Labs said in a report. The malware, which gets its name from an embedded URL to a YouTube rap music video in an earlier version, is said to have amassed a growing collection of compromised SSH servers, with over 3,500 unique IP addresses used to scan and brute-force their way into the servers.

A new ransomware family called 'GwisinLocker' targets South Korean healthcare, industrial, and pharmaceutical companies with Windows and Linux encryptors, including support for encrypting VMware ESXi servers and virtual machines. On Wednesday, Korean cybersecurity experts at Ahnlab published a report on the Windows encryptor, and yesterday, security researchers at ReversingLabs published their technical analysis of the Linux version.

A new botnet called 'RapperBot' is being used in attacks since mid-June 2022, focusing on brute-forcing its way into Linux SSH servers to establish a foothold on the device. Over the past 1.5 months since its discovery, the new botnet used over 3,500 unique IPs worldwide to scan and attempt brute-forcing Linux SSH servers.

A never-before-seen Linux malware has been dubbed a "Swiss Army Knife" for its modular architecture and its capability to install rootkits. This previously undetected Linux threat, called Lightning Framework by Intezer, is equipped with a plethora of features, making it one of the most intricate frameworks developed for targeting Linux systems.

A new and previously undetected malware dubbed 'Lightning Framework' targets Linux systems and can be used to backdoor infected devices using SSH and deploy multiple types of rootkits. Described as a "Swiss Army Knife" in a report published today by Intezer, Lightning Framework is a modular malware that also comes with support for plugins.

Kaspersky security researchers have disclosed details of a brand-new ransomware family written in Rust, making it the third strain after BlackCat and Hive to use the programming language. Luna, as it's called, is "Fairly simple" and can run on Windows, Linux, and ESXi systems, with the malware banking on a combination of Curve25519 and AES for encryption.