Security News

Microsoft has released Windows Subsystem for Linux 2.0.0 with a set of new opt-in experimental features, including a new network mode and automated memory and disk size cleanup. This WSL update introduces "Mirrored mode networking," a new networking mode that not only brings new capabilities but also enhances network compatibility.

A Chinese espionage-focused hacker tracked as 'Earth Lusca' was observed targeting government agencies in multiple countries, using a new Linux backdoor dubbed 'SprySOCKS.'. Trend Micro's analysis of the novel backdoor showed that it originates from the Trochilus open-source Windows malware, with many of its functions ported to work on Linux systems.
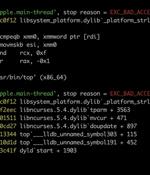
A set of memory corruption flaws have been discovered in the ncurses programming library that could be exploited by threat actors to run malicious code on vulnerable Linux and macOS systems. "Using environment variable poisoning, attackers could chain these vulnerabilities to elevate privileges and run code in the targeted program's context or perform other malicious actions," Microsoft Threat Intelligence researchers Jonathan Bar Or, Emanuele Cozzi, and Michael Pearse said in a technical report published today.
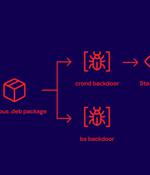
A download manager site served Linux users malware that stealthily stole passwords and other sensitive information for more than three years as part of a supply chain attack. The modus operandi entailed establishing a reverse shell to an actor-controlled server and installing a Bash stealer on the compromised system.

A reported Free Download Manager supply chain attack redirected Linux users to a malicious Debian package repository that installed information-stealing malware. BleepingComputer has also contacted the vendor of Free Download Manager for a comment, but we haven't heard back by publication time.

Linux is a powerful and customizable operating system that has been the backbone of many businesses for decades. This policy from TechRepublic Premium provides guidelines for securing Linux on...

Offensive Security has released Kali Linux 2023.3, the latest version of its penetration testing and digital forensics platform.Besides updates to current tools, new versions of Kali typically introduce fresh tools.

Kali Linux 2023.3, the third version of 2023, is now available for download, with nine new tools and internal optimizations. Kali Linux is a Linux distribution created for ethical hackers and cybersecurity professionals to perform penetration testing, security audits, and research against networks.

How to Quickly Give Users sudo Privileges in Linux If you have users that need certain admin privileges on your Linux machines, here's a walk-through of the process for granting full or specific rights. How many times have you created a new user on a Linux machine, only to find out that new user doesn't have sudo privileges? Without the ability to use sudo, that user is limited in what they can do.

The threat actors behind the Monti ransomware have resurfaced after a two-month break with a new Linux version of the encryptor in its attacks targeting government and legal sectors. Monti emerged in June 2022, weeks after the Conti ransomware group shut down its operations, deliberately imitating the tactics and tools associated with the latter, including its leaked source code.