Security News

A newly patched security flaw in Microsoft Windows was exploited as a zero-day by Lazarus Group, a prolific state-sponsored actor affiliated with North Korea. The security vulnerability, tracked...

The North Korea-linked threat actor known as Lazarus Group employed its time-tested fabricated job lures to deliver a new remote access trojan called Kaolin RAT. The malware could, "aside from...

Research into Lazarus Group's attacks using Log4Shell has revealed novel malware strains written in an atypical programming language. At least three new DLang-based malware strains have been used in attacks on worldwide organizations spanning the manufacturing, agriculture, and physical security industries, Cisco Talos revealed today.

The notorious North Korea-linked threat actor known as the Lazarus Group has been attributed to a new global campaign that involves the opportunistic exploitation of security flaws in Log4j to...

Threat actors from the Democratic People's Republic of Korea (DPRK) are increasingly targeting the cryptocurrency sector as a major revenue generation mechanism since at least 2017 to get around...

The North Korea-aligned Lazarus Group has been attributed as behind a new campaign in which an unnamed software vendor was compromised through the exploitation of known security flaws in another...

The North Korea-linked Lazarus Group (aka Hidden Cobra or TEMP.Hermit) has been observed using trojanized versions of Virtual Network Computing (VNC) apps as lures to target the defense industry...

As much as $7 billion in cryptocurrency has been illicitly laundered through cross-chain crime, with the North Korea-linked Lazarus Group linked to the theft of roughly $900 million of those...
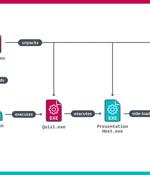
The North Korea-linked Lazarus Group has been linked to a cyber espionage attack targeting an unnamed aerospace company in Spain in which employees of the firm were approached by the threat actor...
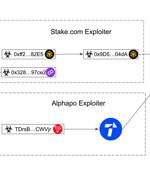
The North Korea-affiliated Lazarus Group has stolen nearly $240 million in cryptocurrency since June 2023, marking a significant escalation of its hacks. According to multiple reports from Certik, Elliptic, and ZachXBT, the infamous hacking group is said to be suspected behind the theft of $31 million in digital assets from the CoinEx exchange on September 12, 2023.