Security News

A North Korean satellite allegedly designed for reconnaissance was not viable for its alleged intended purpose, according to South Korea's military on Wednesday. North Korea attempted to put the satellite into orbit on May 31, but it instead plunged into the sea soon after it was launched.

North Korea has created a fake version of South Korea's largest internet portal, Naver, in a large scale phishing attempt, Seoul's National Intelligence Service said on Wednesday. NIS has asked the Korea Internet & Security Agency to shut down the now inaccessible phishing site.

The North Korean criminal gang Lazarus Group has been blamed for last weekend's attack on Atomic Wallet that drained at least $35 million in cryptocurrency from private accounts. The researchers added that the "Stolen assets are being laundered using specific services, including the Sinbad mixer, which have also been used to launder the proceeds of past hacks perpetrated by the Lazarus Group." In addition, the stolen assets were mingled in wallets that also hold cryptocurrency stolen in previous attacks by the Lazarus Group.

"Successful compromises of the targeted individuals enable Kimsuky actors to craft more credible and effective spear-phishing emails that can be leveraged against sensitive, high-value targets." Kimsuky refers to an ancillary element within North Korea's Reconnaissance General Bureau and is known to collect tactical intelligence on geopolitical events and negotiations affecting the regime's interests.

The United States and the Republic of Korea have issued a joint cyber security advisory [PDF] about North Koreas "Kimsuky" cyber crime group. In their joint advisory, US and South Korean authorities said Kimsuky targets "Think tanks, academic institutions, and news outlets for the purpose of intelligence gathering." The South says the gang is also involved in stealing info used by the DPRK's satellite program.

The Treasury Department's Office of Foreign Assets Control announced sanctions today against four entities and one individual for their involvement in illicit IT worker schemes and cyberattacks generating revenue to finance North Korea's weapons development programs. North Korea's illicit revenue generation strategy relies heavily on a massive "Army" of thousands of IT workers who hide their identities to get hired by companies overseas, the OFAC said in a press release published on Tuesday.
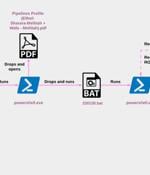
The North Korean threat actor known as ScarCruft began experimenting with oversized LNK files as a delivery route for RokRAT malware as early as July 2022, the same month Microsoft began blocking macros across Office documents by default. Other bespoke malware used by the group include, but not limited to, Chinotto, BLUELIGHT, GOLDBACKDOOR, Dolphin, and, most recently, M2RAT. It's also known to use commodity malware such as Amadey, a downloader that can receive commands from the attacker to download additional malware, in a bid to confuse attribution.

The US government is aggressively pursuing three men accused of wide-ranging and complex conspiracies of laundering stolen and illicit cryptocurrency that the North Korean regime used to finance its massive weapons programs. The Department of Justice this month indicted North Korean national Sim Hyon Sop, Wu HuiHui of China, and Cheng Hung Man, a Hong Kong British national, for their roles in two money laundering conspiracies, both aimed at channeling funds into North Korea's coffers.

According to Mandiant, who has tracked APT43 since 2018, the threat actor aligns with the mission of the Reconnaissance General Bureau, the main foreign intelligence service from North Korea. In particular, malware and tools have been shared between APT43 and the infamous Lazarus threat actor.

Researchers at Russian cybersecurity firm Kaspersky today revealed that they identified a small number of cryptocurrency-focused firms as at least some of the victims of the 3CX software supply-chain attack that's unfolded over the past week. Kaspersky declined to name any of those victim companies, but it notes that they're based in "Western Asia.".