Security News

The increased proliferation of IoT devices paved the way for the rise of IoT botnets that amplifies DDoS attacks today. Cybercriminals use botnets for various malicious purposes, most significantly for DDoS attacks against targets.

"This sector has a lot of proprietary IoT and industrial automation at the edge but it's not very easy for them to manage. Now they're evolving the application they got from equipment makers such as ABB, Bosch, or Siemens to run on a mainstream compute platform." Hood calls this the industrial 'device edge', an incarnation of edge computing in which large numbers of devices are connected directly to local computing resources rather than having to backhaul traffic to distant datacenters.

The DCMS helped fund the roll out of assurance schemes leading to IASME launching its IoT Security Assured Scheme in 2021. The theory is that the product assurance scheme will spur compliance ahead of the PSTI, making the transition that much easier for the IoT industry, and the fact that many have aimed high suggests the approach is working.
A newly designed privacy-sensitive architecture aims to enable developers to create smart home apps in a manner that addresses data sharing concerns and puts users in control over their personal information. Peekaboo operates on the principle of data minimization, which refers to the practice of limiting data collection to only what is required to fulfill a specific purpose.
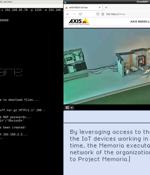
Called Ransomware for IoT or R4IoT by Forescout, it's a "Novel, proof-of-concept ransomware that exploits an IoT device to gain access and move laterally in an IT network and impact the OT network." This potential pivot is based on the rapid growth in the number of IoT devices as well as the convergence of IT and OT networks in organizations.

The security firm's Vedere Labs team said it developed a proof-of-concept strain of this type of next-generation malware, which they called R4IoT. After gaining initial access via IoT devices, the malware moves laterally through the IT network, deploying ransomware and cryptocurrency miners while also exfiltrating data, before taking advantage of operational technology systems to potentially physically disrupt critical business operations, such as pipelines or manufacturing equipment. These types of increasingly destructive attacks, combined with the growing number of internet-connected devices led the researchers to consider: what if ransomware exploited IoT gear to get into a corporate network.

A group of academics has devised a system that can be used on a phone or a laptop to identify and locate Wi-Fi-connected hidden IoT devices in unfamiliar physical spaces. With hidden cameras being increasingly used to snoop on individuals in hotel rooms and Airbnbs, the goal is to be able to pinpoint such rogue devices without much of a hassle.

A fresh look at the Fronton DDoS-focused botnet reveals the criminal tool has more capabilities than previously known. The Fronton botnet first made the headline in March 2020.

"This system includes a web-based dashboard known as SANA that enables a user to formulate and deploy trending social media events en masse. The system creates these events that it refers to as Инфоповоды, 'newsbreaks,' utilizing the botnet as a geographically distributed transport." The existence of Fronton, an IoT botnet, became public knowledge following revelations from BBC Russia and ZDNet in March 2020 after a Russian hacker group known as Digital Revolution published documents that it claimed were obtained after breaking into a subcontractor to the FSB, the Federal Security Service of the Russian Federation.

An unpatched Domain Name System bug in a popular standard C library can allow attackers to mount DNS poisoning attacks against millions of IoT devices and routers to potentially take control of them, researchers have found. "The flaw is caused by the predictability of transaction IDs included in the DNS requests generated by the library, which may allow attackers to perform DNS poisoning attacks against the target device," Nozomi's Giannis Tsaraias and Andrea Palanca wrote in the post.