Security News

Organizations need to be aware of the cybersecurity blind spots generated by the prevalence of IoT technology, because connected devices are opening virtual doors into organizations' networks. As IoT adoption becomes more widespread, 93% of enterprises are finding it necessary to up their security spend for IoT and unmanaged devices as a result.

In this Help Net Security video, Brian Contos, CSO at Phosphorus Cybersecurity, discusses how most companies consider IoT threats to be limited in scope. In actuality, a growing number of sophisticated adversaries are realizing the true value of IoT as an easy initial breach point to get access to the corporate network.

Fears over security have become less of a concern for organizations adopting IoT solutions than it was five years ago, according to a recent study by Wi-SUN Alliance, a global member-based association of industry leading companies driving the adoption of interoperable wireless solutions for use in smart cities, smart utilities, IoT and industrial IoT applications. The Journey to IoT Maturity, a follow-up to Wi-SUN's 'state of the nation' IoT study in 2017, is based on interviews with IT decision makers from UK and US IoT adopters within key industries, including energy and utilities, state and local government, construction, technology, and telecommunications.
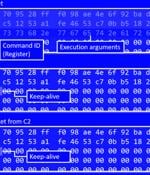
"This family borrows heavily from the original Mirai source code, but what separates it from other IoT malware families is its built-in capability to brute force credentials and gain access to SSH servers instead of Telnet as implemented in Mirai," Fortinet FortiGuard Labs said in a report. The malware, which gets its name from an embedded URL to a YouTube rap music video in an earlier version, is said to have amassed a growing collection of compromised SSH servers, with over 3,500 unique IP addresses used to scan and brute-force their way into the servers.

The increased proliferation of IoT devices paved the way for the rise of IoT botnets that amplifies DDoS attacks today. Cybercriminals use botnets for various malicious purposes, most significantly for DDoS attacks against targets.

"This sector has a lot of proprietary IoT and industrial automation at the edge but it's not very easy for them to manage. Now they're evolving the application they got from equipment makers such as ABB, Bosch, or Siemens to run on a mainstream compute platform." Hood calls this the industrial 'device edge', an incarnation of edge computing in which large numbers of devices are connected directly to local computing resources rather than having to backhaul traffic to distant datacenters.

The DCMS helped fund the roll out of assurance schemes leading to IASME launching its IoT Security Assured Scheme in 2021. The theory is that the product assurance scheme will spur compliance ahead of the PSTI, making the transition that much easier for the IoT industry, and the fact that many have aimed high suggests the approach is working.
A newly designed privacy-sensitive architecture aims to enable developers to create smart home apps in a manner that addresses data sharing concerns and puts users in control over their personal information. Peekaboo operates on the principle of data minimization, which refers to the practice of limiting data collection to only what is required to fulfill a specific purpose.
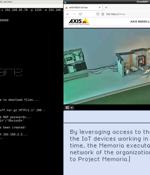
Called Ransomware for IoT or R4IoT by Forescout, it's a "Novel, proof-of-concept ransomware that exploits an IoT device to gain access and move laterally in an IT network and impact the OT network." This potential pivot is based on the rapid growth in the number of IoT devices as well as the convergence of IT and OT networks in organizations.

The security firm's Vedere Labs team said it developed a proof-of-concept strain of this type of next-generation malware, which they called R4IoT. After gaining initial access via IoT devices, the malware moves laterally through the IT network, deploying ransomware and cryptocurrency miners while also exfiltrating data, before taking advantage of operational technology systems to potentially physically disrupt critical business operations, such as pipelines or manufacturing equipment. These types of increasingly destructive attacks, combined with the growing number of internet-connected devices led the researchers to consider: what if ransomware exploited IoT gear to get into a corporate network.