Security News

Microsoft says a Chinese cyberespionage group it tracks as Volt Typhoon has been targeting critical infrastructure organizations across the United States, including Guam, since at least mid-2021. "Microsoft assesses with moderate confidence that this Volt Typhoon campaign is pursuing development of capabilities that could disrupt critical communications infrastructure between the United States and Asia region during future crises," the Microsoft Threat Intelligence team said.

Cybersecurity researchers have unearthed previously undocumented attack infrastructure used by the prolific state-sponsored group SideWinder to strike entities located in Pakistan and China. SideWinder has been known to be active since at least 2012, with attack chains primarily leveraging spear-phishing as an intrusion mechanism to obtain a foothold into targeted environments.

A new risk emerges in the digital era, where open-source software has become a fundamental pillar in developing innovative applications. In this Help Net Security video, Henrik Plate, Lead Security Researcher at Endor Labs, discusses the dual-edged nature of open-source software.

The U.S. Justice Department has filed charges against a Russian citizen named Mikhail Pavlovich Matveev for involvement in three ransomware operations that targeted victims across the United States. "Matveev is responsible for multiple ransomware variants as an affiliate and has actively targeted U.S. businesses and critical infrastructure," FBI Special Agent James E. Dennehy said in a press conference today.
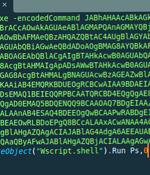
A previously undetected advanced persistent threat actor dubbed Red Stinger has been linked to attacks targeting Eastern Europe since 2020. Red Stinger overlaps with a threat cluster Kaspersky revealed under the name Bad Magic last month as having targeted government, agriculture, and transportation organizations located in Donetsk, Lugansk, and Crimea last year.

Threats - from cybersecurity exploits to climate change - have major implications for those systems, and with emerging technologies only increasing demand for power and creating new vulnerabilities, maintaining infrastructure is as much about resiliency as keeping the juice flowing, the air conditioners running and the security cameras pointed at the door. Joseph Vijay, CEO of Intelli-Systems, a Melbourne, Australia-based critical systems infrastructure company that supports infrastructure for mines, hospitals, data centers and more, said buyers of critical infrastructure need to focus more on how the infrastructure purchase decisions they make will influence both their bottom line and the environment.

ETHOS is still under initial cooperative development, the nonprofit entity behind the project said in a press release, with founding members including OT and ICS security firms and tech consultancies such as 1898 & Co., Claroty, NetRise, and Schneider Electric. The companies founded ETHOS in response to Uncle Sam's CISA's Shields Up initiative and the Biden administration's various 100 day sprints to improve cybersecurity in critical sectors.

Lazarus, the prolific North Korean hacking group behind the cascading supply chain attack targeting 3CX, also breached two critical infrastructure organizations in the power and energy sector and two other businesses involved in financial trading using the trojanized X TRADER application. The new findings, which come courtesy of Symantec's Threat Hunter Team, confirm earlier suspicions that the X TRADER application compromise affected more organizations than 3CX. The names of the organizations were not revealed.

The X Trader software supply chain attack that led to last month's 3CX breach has also impacted at least several critical infrastructure organizations in the United States and Europe, according to Symantec's Threat Hunter Team. While the Trading Technologies supply chain compromise is the result of a financially motivated campaign, the breach of multiple critical infrastructure organizations is worrisome, seeing that North Korean-backed hacking groups are also known for cyber espionage.

Experts say the attacks demonstrate the risk that fairly unsophisticated attacks pose even to well-defended enterprises and that other countries should take notice and prepare. Starting before the annual OpIsrael hacktivist assault on Israeli enterprises from April 6 to 9, Israel experienced recent attacks by Russian entities like Killnet and Anonymous Sudan, a cybersecurity bugbear for Israel this year.