Security News
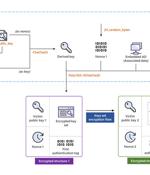
The operators of the Hive ransomware-as-a-service scheme have overhauled their file-encrypting software to fully migrate to Rust and adopt a more sophisticated encryption method. "With its latest variant carrying several major upgrades, Hive also proves it's one of the fastest evolving ransomware families, exemplifying the continuously changing ransomware ecosystem," Microsoft Threat Intelligence Center said in a report on Tuesday.

The Hive group, which has become one of the most prolific ransomware-as-a-service operators, has significantly overhauled its malware, including migrating the code to the Rust programming language and using a more complex file encryption process. "With its latest variant carrying several major upgrades, Hive also proves it's one of the fastest evolving ransomware families, exemplifying the continuously changing ransomware ecosystem," the researchers said in a write-up this week.

All computer systems on the network of Costa Rica's public health service are now offline following a Hive ransomware attack that hit them this morning. The incident comes after Costa Rica declared a national emergency following Conti ransomware attacks that hit multiple government bodies, including the Costa Rican Social Security Fund.

An analysis of four months of chat logs spanning more than 40 conversations between the operators of Conti and Hive ransomware and their victims has offered an insight into the groups' inner workings and their negotiation techniques. Conti and Hive are among the most prevalent ransomware strains in the threat landscape, cumulatively accounting for 29.1% of attacks detected during the three-month-period between October and December 2021.

Ransomware attacks increased over 50% from February to March, and Hive was identified as the third-most active hacking group over the last month. Hive saw a 188% increase in the number of attacks from February, showing the most growth in rate of attacks during the last month as well.

An affiliate of the aggressive Hive ransomware group is exploiting known vulnerabilities in Microsoft Exchange servers to encrypt and exfiltrate data and threaten to publicly disclose the information if the ransom isn't paid. In a recent attack on an unnamed organization, the Hive affiliate rapidly compromised multiple devices and file servers by exploiting the ProxyShell vulnerabilities in Exchange servers, encrypting the data within 72 hours of the start of the attack, threat hunters with data security vendor Varonis Systems said in a report this week.

A recent Hive ransomware attack carried out by an affiliate involved the exploitation of "ProxyShell" vulnerabilities in the Microsoft Exchange Server that were disclosed last year to encrypt an unnamed customer's network. "The actor managed to achieve its malicious goals and encrypt the environment in less than 72 hours from the initial compromise," Varonis security researcher, Nadav Ovadia, said in a post-mortem analysis of the incident.

A Hive ransomware affiliate has been targeting Microsoft Exchange servers vulnerable to ProxyShell security issues to deploy various backdoors, including Cobalt Strike beacon. From there, the threat actors perform network reconnaissance, steal admin account credentials, exfiltrate valuable data, ultimately deploying the file-encrypting payload. The details come from security and analytics company Varonis, who was called in to investigate a ransomware attack on one of its customers.

Threat analysts have discovered a new obfuscation technique used by the Hive ransomware gang, which involves IPv4 addresses and a series of conversions that eventually lead to downloading a Cobalt Strike beacon. There are numerous ways to achieve obfuscation, each with its own set of pros and cons, but a novel one discovered in a an incident response involving Hive ransomware shows that adversaries are finding new, stealthier ways to achieve their goal.

The Hive ransomware operation has converted their VMware ESXi Linux encryptor to the Rust programming language and added new features to make it harder for security researchers to snoop on victim's ransom negotiations. Ransomware gang's Linux encryptors typically target the VMware ESXI virtualization platforms as they are the most commonly used in the enterprise.