Security News

The sheriff of a small city in Florida warned on Monday that hackers had tried to poison its water. Pinellas County Sheriff Bob Gualtieri said Oldsmar's water treatment system, which serves roughly 15,000 people, was broken into by someone, via the internet, who had hoped to flood the supply with levels of sodium hydroxide more than 100 times the normal amount.
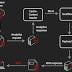
New details have emerged about a vast network of rogue extensions for Chrome and Edge browsers that were found to hijack clicks to links in search results pages to arbitrary URLs, including phishing sites and ads. Collectively called "CacheFlow" by Avast, the 28 extensions in question - including Video Downloader for Facebook, Vimeo Video Downloader, Instagram Story Downloader, VK Unblock - made use of a sneaky trick to mask its true purpose: Leverage Cache-Control HTTP header as a covert channel to retrieve commands from an attacker-controlled server.

Seven vulnerabilities have been found in a popular DNS caching proxy and DHCP server known as dnsmasq, raising the possibility of widespread online attacks on networking devices. Dnsmasq 2.83, maintained by open source software developer Simon Kelley, has been released to address the issues, which recall the DNS cache poisoning vulnerability identified in 2008 by security researcher Dan Kaminsky.

The set of seven flaws are comprised of buffer overflow issues and flaws allowing for DNS cache-poisoning attacks. If exploited, these flaws could be chained together to allow remote code execution, denial of service and other attacks.

Online surveys and form building software as a service Typeform has patched an information hijacking vulnerability. The flaw which existed in Typeform's Zendesk Sell app integration could let attackers quietly redirect form submissions with potentially sensitive data to themselves.

Makers of the Chrome, Firefox and Edge browsers are urging users to patch critical vulnerabilities that if exploited allow hackers to hijack systems running the software. The Mozilla Firefox vulnerability is separate from a bug reported in Google's browser engine Chromium, which is used in the Google Chrome browser and Microsoft's latest version of its Edge browser.

Reseachers are raising the alarm for a newly identified operation leveraging a new Remote Access Tool written in Golang to steal crypto-currency from unsuspecting users. Discovered last month, the campaign is believed to have been active since January 2020, consisting of a fully-fledged marketing campaign, custom applications related to crypto-currency, fake social media accounts, websites, and the new RAT, which Intezer calls ElectroRAT. Widely undetected, the Golang backdoor is written from scratch and is designed to target Windows, Linux, and macOS. To lure crypto-currency users into downloading Trojanized apps, the threat actor behind the campaign promoted the tools on crypto-currency and blockchain forums, as well as on social media platforms.

Microsoft on Thursday took the wraps off an ongoing campaign impacting popular web browsers that stealthily injects malware-infested ads into search results to earn money via affiliate advertising. The campaign - which impacts Microsoft Edge, Google Chrome, Yandex Browser, and Mozilla Firefox browsers on Windows - aims to insert additional, unauthorized ads on top of legitimate ads displayed on search engine results pages, leading users to click on these ads inadvertently.

For at least the third time in its existence, OGUsers - a forum overrun with people looking to buy, sell and trade access to compromised social media accounts - has been hacked. Roughly a week ago, the OGUsers homepage was defaced with a message stating the forum's user database had been compromised.

Attackers are compromising email accounts from popular universities, including Purdue and Oxford, to launch attacks that get around DMARC and SPF. Cybercriminals are hijacking legitimate email accounts from more than a dozen universities - including Purdue University, University of Oxford in the U.K. and Stanford University - and using the accounts to bypass detection and trick victims into handing over their email credentials or installing malware. The highest number of phishing emails detected came from compromised Purdue University accounts, stolen in campaigns from Jan. to Sept. Behind Purdue University was Oxford, Hunter College and Worcester Polytechnic Institute.