Security News

Microsoft, a week after disclosing that Kremlin-backed spies broke into its network and stole internal emails and files from its executives and staff, has now confirmed the compromised corporate account used in the genesis of the heist didn't even have multi-factor authentication enabled. On Thursday, Redmond admitted Midnight Blizzard - a Moscow-supported espionage team also known as APT29 or Cozy Bear - "Utilized password spray attacks that successfully compromised a legacy, non-production test tenant account that did not have multifactor authentication enabled."

The Akira ransomware gang is claiming responsiblity for the "Cybersecurity incident" at British bath bomb merchant. Akira says it has stolen 110 GB of data from the UK-headquartered global cosmetics giant, which has more than 900 stores worldwide, allegedly including "a lot of personal documents" such as passport scans.

Threat actors affiliated with the Democratic People's Republic of Korea (also known as North Korea) have plundered at least $600 million in cryptocurrency in 2023. The DPRK "was responsible for...

Miscreants took over security giant Mandiant's Twitter account for several hours on Wednesday in an attempt to steal cryptocurrency, then trolled the Google-owned security shop, telling its admins to change the password. "We are aware of the incident that impacted the Mandiant X account and are conducting a thorough investigation," a spokesperson told The Register.

While still a chief petty officer, Marquis Hooper accessed a database containing millions of records and over the course of five months sold details of more than 9,000 people online. Prosecutors said the total sum generated by Hooper and his wife, Natasha Chalk, co-defendant in the case and former Navy reservist, reached the equivalent of $160,000 in Bitcoin.

Chinese snoops stole about 60,000 State Department emails when they broke into Microsoft-hosted Outlook and Exchange Online accounts belonging to US government officials over the summer. "No classified systems were hacked," said State Department spokesperson Matthew Miller during a press briefing Thursday.

Mixin Network confirmd on Monday that it has "Temporarily suspended" all deposit and withdrawal services after hackers broke into a database and stole about $200 million in funds from the Hong-Kong based cryptocurrency firm. In a statement posted on the social media platform formerly known as Twitter, the digital biz said the incident happened early Saturday morning, when "The database of Mixin Network's cloud service provider was attacked by hackers. After initial verification, the funds involved are approximately US$200 million."

Kosi Goodness Simon-Ebo, a 29-year-old Nigerian national extradited from Canada to the United States last April, pleaded guilty to wire fraud and money laundering through business email compromise. According to the plea agreement, the scammers had a high success ratio of roughly 1 to 7, making one million out of the almost seven million they attempted to steal.
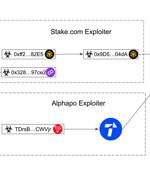
The North Korea-affiliated Lazarus Group has stolen nearly $240 million in cryptocurrency since June 2023, marking a significant escalation of its hacks. According to multiple reports from Certik, Elliptic, and ZachXBT, the infamous hacking group is said to be suspected behind the theft of $31 million in digital assets from the CoinEx exchange on September 12, 2023.

The U.S. Federal Bureau of Investigation on Tuesday warned that threat actors affiliated with North Korea may attempt to cash out stolen cryptocurrency worth more than $40 million. North Korea is known to blur the lines among cyber warfare, espionage, and financial crime.