Security News

Nation-state operators with nexus to Iran are increasingly turning to ransomware as a means of generating revenue and intentionally sabotaging their targets, while also engaging in patient and persistent social engineering campaigns and aggressive brute force attacks. No less than six threat actors affiliated with the West Asian country have been discovered deploying ransomware to achieve their strategic objectives, researchers from Microsoft Threat Intelligence Center revealed, adding "These ransomware deployments were launched in waves every six to eight weeks on average."

The Microsoft Threat Intelligence Center has presented an analysis of the evolution of several Iranian threat actors at the CyberWarCon 2021, and their findings show increasingly sophisticated attacks. Since September 2020, Microsoft has been tracking six Iranian hacking groups deploying ransomware and exfiltrating data to cause disruption and destruction for victims.

Develop the necessary skills and use the tools to be an ethical hacker through this 120-hour comprehensive course bundle. Penetration testers are another word for ethical hackers, and they're incredibly in demand.

I just don't think it's possible to create a hack-proof computer system, especially when the system is physically in the hands of the hackers. Hackers may have just made some big strides towards possibly jailbreaking the PlayStation 5 over the weekend, with the hacking group Fail0verflow claiming to have managed to obtain PS5 root keys allowing them to decrypt the console's firmware.
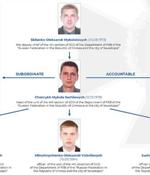
Ukraine's premier law enforcement and counterintelligence agency on Thursday disclosed the real identities of five individuals allegedly involved in digital intrusions attributed to a cyber-espionage group named Gamaredon, linking the members to Russia's Federal Security Service. Calling the hacker group "An FSB special project, which specifically targeted Ukraine," the Security Service of Ukraine said the perpetrators "Are officers of the 'Crimean' FSB and traitors who defected to the enemy during the occupation of the peninsula in 2014.".
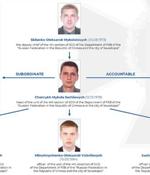
Ukraine's premier law enforcement and counterintelligence agency on Thursday disclosed the real identities of five individuals allegedly involved in cyberattacks attributed to a cyber-espionage group named Gamaredon, linking the members to Russia's Federal Security Service. Calling the hacker group "An FSB special project, which specifically targeted Ukraine," the Security Service of Ukraine said the perpetrators "Are officers of the 'Crimean' FSB and traitors who defected to the enemy during the occupation of the peninsula in 2014.".

The Ukrainian cybercrime police force has arrested members of a group of money launderers and hackers at the request of U.S. intelligence services. In a press release by Ukraine's SSU, law enforcement says the individuals engaged in large-scale international operations where they laundered tens of millions of USD for various hacking groups.

The FIN7 hacking group is attempting to join the highly profitable ransomware space by creating fake cybersecurity companies that conduct network attacks under the guise of pentesting. As ransomware has become a profitable field for cybercriminals, and having previous experience with fake front companies like "Combi Security", the group set up a new firm to lure legitimate IT specialists.

The U.S. Commerce Department on Wednesday announced new rules barring the sales of hacking software and equipment to authoritarian regimes and potentially facilitate human rights abuse for national security and anti-terrorism reasons. "The United States Government opposes the misuse of technology to abuse human rights or conduct other malicious cyber activities, and these new rules will help ensure that U.S. companies are not fueling authoritarian practices," BIS said in a press release.

The Commerce Department's Bureau of Industry and Security today announced new controls that would ban U.S. companies from exporting and reselling software and hardware tools that could be used to fuel authoritarian practices through malicious hacking activities and human rights abuse.The rule will become effective in 90 days and will effectively ban the export of "Cybersecurity items" for National Security and Anti-terrorism reasons.