Security News
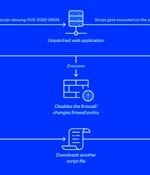
A now-patched critical security flaw affecting Atlassian Confluence Server that came to light a few months ago is being actively exploited for illicit cryptocurrency mining on unpatched installations. In one of the infection chains observed by the cybersecurity company, the flaw was leveraged to download and run a shell script on the victim's machine, which, in turn, fetched a second shell script.

The Federal Bureau of Investigation and CISA said that one of the Iranian threat groups behind the destructive attack on the Albanian government's network in July lurked inside its systems for roughly 14 months. "A FBI investigation indicates Iranian state cyber actors acquired initial access to the victim's network approximately 14 months before launching the destructive cyber attack, which included a ransomware-style file encryptor and disk wiping malware," the two agencies revealed in a joint advisory published today.

Digital assets trading firm Wintermute has been hacked and lost $162.2 million in DeFi operations, the company CEO, Evgeny Gaevoy, announced earlier today. Wintermute provides liquidity to over 50 cryptocurrency exchanges and trading platforms, including Binance, Coinbase, Kraken, and Bitfinex.

A threat cluster linked to the Russian nation-state actor tracked as Sandworm has continued its targeting of Ukraine with commodity malware by masquerading as telecom providers, new findings show. Recorded Future said it discovered new infrastructure belonging to UAC-0113 that mimics operators like Datagroup and EuroTransTelecom to deliver payloads such as Colibri loader and Warzone RAT. The attacks are said to be an expansion of the same campaign that previously distributed DCRat using phishing emails with legal aid-themed lures against providers of telecommunications in Ukraine.

An MFA Fatigue attack is when a threat actor runs a script that attempts to log in with stolen credentials over and over, causing what feels like an endless stream of MFA push requests to be sent to the account's owner's mobile device. A demonstration of an MFA Fatigue attack, or MFA spam, can be seen in this YouTube video created by cybersecurity support company Reformed IT. In many cases, the threat actors will push out repeated MFA notifications and then contact the target through email, messaging platforms, or over the phone, pretending to be IT support to convince the user to accept the MFA prompt.

The Russian state-sponsored hacking group known as Sandworm has been observed masquerading as telecommunication providers to target Ukrainian entities with malware. Sandworm is a state-backed threat actor attributed by the US government as part of the Russian GRU foreign military intelligence service.

American video game publisher Rockstar Games on Monday revealed it was a victim of a "Network intrusion" that allowed an unauthorized party to illegally download early footage for the Grand Theft Auto VI. "At this time, we do not anticipate any disruption to our live game services nor any long-term effect on the development of our ongoing projects," the company said in a notice shared on its social media handles. The company said that the third-party accessed "Confidential information from our systems," although it's not immediately clear if it involved any other data beyond the game footage.

Become an ethical hacker online We may be compensated by vendors who appear on this page through methods such as affiliate links or sponsored partnerships. Whether you're running a business worried about cybercrime or looking to earn some more money, becoming an ethical hacker can be a big boost.

Password management solution LastPass shared more details pertaining to the security incident last month, disclosing that the threat actor had access to its systems for a four-day period in August 2022. "There is no evidence of any threat actor activity beyond the established timeline," LastPass CEO Karim Toubba said in an update shared on September 15, adding, "There is no evidence that this incident involved any access to customer data or encrypted password vaults."

LastPass says the attacker behind the August security breach had internal access to the company's systems for four days until they were detected and evicted. While method through which the attacker was able to compromise a Lastpass developer's endpoint to access the Development environment, the investigation found that the threat actor was able to impersonate the developer after he "Had successfully authenticated using multi-factor authentication."