Security News

Another link discovered by Group-IB downloaded from Google Play, the official Android app store, a fake version of the 'Secure VPN' app, which is still present on Google Play at the time of writing and has just over 10 downloads. The researchers note that the description available for SideWinder's fake Secure VPN app has been copied from the legitimate NordVPN app.
A new set of trojanized apps spread via the Google Play Store has been observed distributing the notorious Joker malware on compromised Android devices. Despite continued attempts on the part of Google to scale up its defenses, the apps have been continually iterated to search for gaps and slip into the app store undetected.

Google is now blocking Russian users and developers from downloading or updating paid applications from the Google Play Store starting Thursday due to sanctions. "As part of our compliance efforts, Google Play is blocking the downloading of paid apps and updates to paid apps in Russia starting May 5, 2022," the company said in an update on its support website.

Google is rolling out a new Data Safety section on the Play Store, Android's official app repository, where developers must declare what data their software collects from users of their apps. Not only will developers declare what data they collect, but also what data they share with third parties, essentially disclosing the purpose behind the collection.

A popular Windows 11 ToolBox script used to add the Google Play Store to the Android Subsystem has secretly infected users with malicious scripts, Chrome extensions, and potentially other malware. While there were ways to use ADB to sideload Android apps, users began looking for methods that let them add the Google Play Store to Windows 11.

Google pulled a slew of Android apps with more than 46 million downloads from its Google Play Store after security researchers notified the cloud giant that the code contained some sneaky data-harvesting code. Google removed the apps as of March 25, but said they could be re-listed if they removed the dodgy code to comply with Google Play Store's rules for collecting users' data.

Researchers have found the info-stealing Android malware Sharkbot lurking unsuspected in the depths of the Google Play store under the cover of anti-virus solutions. While analyzing suspicious applications on the store, the Check Point Research team found what purported to be genuine AV solutions downloading and installing the malware, which steals credentials and banking info from Android devices but also has a range of other unique features.
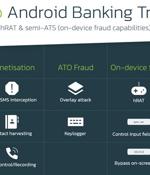
A number of rogue Android apps that have been cumulatively installed from the official Google Play Store more than 50,000 times are being used to target banks and other financial entities. Like other Android banking trojans, the rogue apps are nothing more than droppers, whose primary function is to deploy the malicious payload embedded within them.
As many as seven malicious Android apps discovered on the Google Play Store masqueraded as antivirus solutions to deploy a banking trojan called SharkBot. "SharkBot steals credentials and banking information," Check Point researchers Alex Shamshur and Raman Ladutska said in a report shared with The Hacker News.

A malicious Android app that steals Facebook credentials has been installed over 100,000 times via the Google Play Store, with the app still available to download. The Android malware is disguised as a cartoonifier app called 'Craftsart Cartoon Photo Tools,' allowing users to upload an image and convert it into a cartoon rendering. Over the past week, security researchers and mobile security firm Pradeo discovered that the Android app includes a trojan called 'FaceStealer,' which displays a Facebook login screen that requires users to log in before using the app.