Security News
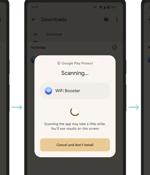
Google has announced an update to its Play Protect with support for real-time scanning at the code level to tackle novel malicious apps prior to downloading and installing them on Android devices....

Google is enhancing Google Play Protect's real-time scanning to include code-level scanning, to keep Android devices safe from malicious and unwanted apps, especially those downloaded from outside of the Google Play app store - whether from third-party app stores or other sources. Google Play Protect, introduced by Google in 2017, is a security suite for Android devices that protects users' devices and data from malicious apps.

Google has announced new, real-time scanning features for Google Play Protect that make it harder for malicious apps employing polymorphism to evade detection. The problem is that authors of malicious apps promoted outside Google Play have resorted to AI and polymorphic malware that frequently alters identifiable information in a malicious program to bypass automated security platforms, making those scans ineffective.

Amazon mistakenly sent out purchase confirmation emails for Hotels.com, Google Play, and Mastercard gift cards to customers, making many worried their accounts were compromised. The emails were sent out last night, with customers reporting receiving three separate emails from Amazon Prime for each alleged gift card purchase.

An app with the name Signal Plus Messenger was available on Play for nine months and had been downloaded from Play roughly 100 times before Google took it down last April after being tipped off by security firm ESET. It was also available in the Samsung app store and on signalplus[. An app calling itself FlyGram was created by the same threat actor and was available through the same three channels.

At the time the researchers published their report, several malicious apps were still available for download through Google Play. The Telegram apps presented in Kaspersky's report are promoted as "Faster" alternatives to the regular app.
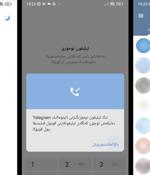
Spyware masquerading as modified versions of Telegram have been spotted in the Google Play Store that's designed to harvest sensitive information from compromised Android devices. The apps have been collectively downloaded millions of times before they were taken down by Google.

ESET researchers have identified two active campaigns targeting Android users, where the threat actors behind the tools for Telegram and Signal are attributed to the China-aligned APT group GREF. Most likely active since July 2020 and since July 2022, respectively for each malicious app, the campaigns have distributed the Android BadBazaar espionage code through the Google Play store, Samsung Galaxy Store, and dedicated websites posing as legitimate encrypted chat applications - the malicious apps are FlyGram and Signal Plus Messenger. Threat actors exploit fake Signal and Telegram apps.

Trojanized Signal and Telegram apps containing the BadBazaar spyware were uploaded onto Google Play and Samsung Galaxy Store by a Chinese APT hacking group known as GREF. [...]

McAfee's Mobile Research Team discovered the malicious Android apps and reported them to Google as they violated Google Play Store's policies. McAfee's report says the adware was hidden in Google Play apps that impersonated the TV/DMB Player, Music Downloader, News, and Calendar applications.