Security News

GitHub is being abused to distribute the Lumma Stealer information-stealing malware as fake fixes posted in project comments. [...]

A critical vulnerability (CVE-2024-6800) affecting all currently supported versions of GitHub Enterprise Server (GHES) may allow attackers to gain unrestricted access to the instance’s contents....

GitHub has released fixes to address a set of three security flaws impacting its Enterprise Server product, including one critical bug that could be abused to gain site administrator privileges....

Unless you're cool with an unauthorized criminal enjoying admin privileges to comb through your code A critical bug in GitHub Enterprise Server could allow an attacker to gain unauthorized access...

A critical vulnerability affecting multiple versions of GitHub Enterprise Server could be exploited to bypass authentication and enable an attacker to gain administrator privileges on the machine. [...]
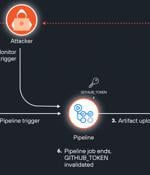
A newly discovered attack vector in GitHub Actions artifacts dubbed ArtiPACKED could be exploited to take over repositories and gain access to organizations' cloud environments."A combination of misconfigurations and security flaws can make artifacts leak tokens, both of third party cloud services and GitHub tokens, making them available for anyone with read access to the repository to consume," Palo Alto Networks Unit 42 researcher Yaron Avital said in a report published this week.

Multiple high-profile open-source projects, including those from Google, Microsoft, AWS, and Red Hat, were found to leak GitHub authentication tokens through GitHub Actions artifacts in CI/CD...

The possibility to integrate security in development processes has given rise to DevSecOps, where development and operations teams work together with security teams and all their processes are converged. The incidents affecting GitHub users in 2023 increased by over 21% compared to the previous year.

Cybersecurity researchers from JFrog recently discovered a GitHub Personal Access Token in a public Docker container hosted on Docker Hub, which granted elevated access to the GitHub repositories of the Python language, Python Package Index, and the Python Software Foundation. The implications of someone finding this leaked token could be extremely severe.

"This network not only distributes malware but also provides various other activities that make these 'Ghost' accounts appear as normal users, lending fake legitimacy to their actions and the associated repositories." These include accounts that serve the phishing repository template, accounts providing the image for the phishing template, and accounts that push malware to the repositories in the form of a password-protected archive masquerading as cracked software and game cheats.