Security News

The Iranian nation-state actor known as MuddyWater has leveraged a newly discovered command-and-control (C2) framework called MuddyC2Go in its attacks on the telecommunications sector in Egypt,...

The Russian nation-state threat actor known as APT28 has been observed making use of lures related to the ongoing Israel-Hamas war to facilitate the delivery of a custom backdoor called HeadLace....

A previously undocumented threat actor has been linked to a cyber attack targeting an aerospace organization in the U.S. as part of what's suspected to be a cyber espionage mission. The BlackBerry...

Russian cyber espionage actors affiliated with the Federal Security Service (FSB) have been observed using a USB propagating worm called LitterDrifter in attacks targeting Ukrainian entities....

Cybersecurity researchers have discovered what they say is malicious cyber activity orchestrated by two prominent Chinese nation-state hacking groups targeting 24 Cambodian government organizations. "This activity is believed to be part of a long-term espionage campaign," Palo Alto Networks Unit 42 researchers said in a report last week.

A threat actor affiliated with Iran's Ministry of Intelligence and Security (MOIS) has been observed waging a sophisticated cyber espionage campaign targeting financial, government, military, and...
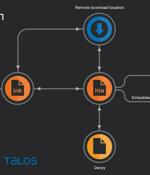
A relatively new threat actor known as YoroTrooper is likely made of operators originating from Kazakhstan. The assessment, which comes from Cisco Talos, is based on their fluency in Kazakh and...

The International Criminal Court provided additional information about the cyberattack five weeks ago, saying that it was a targeted operation for espionage purposes. As an international tribunal, the International Criminal Court is seated in The Hague, Netherlands, and its attributions are to investigate, and to hold accountable individuals committing crimes of concern to the international community.

Government entities in the Asia-Pacific (APAC) region are the target of a long-running cyber espionage campaign dubbed TetrisPhantom. "The attacker covertly spied on and harvested sensitive data...
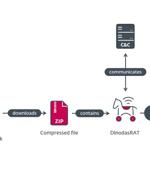
A governmental entity in Guyana has been targeted as part of a cyber espionage campaign dubbed Operation Jacana. The activity, which was detected by ESET in February 2023, entailed a...