Security News

The notorious Emotet malware has returned with renewed vigor as part of a high-volume malspam campaign designed to drop payloads like IcedID and Bumblebee. "Hundreds of thousands of emails per day" have been sent since early November 2022, enterprise security company Proofpoint said last week, adding, "The new activity suggests Emotet is returning to its full functionality acting as a delivery network for major malware families."

The Emotet malware-delivery botnet is back after a short hiatus, quickly ramping up the number of malicious emails it's sending and sporting additional capabilities, including changes to its binary and delivering a new version of the IcedID malware dropper. The various changes after almost four months of silence also could indicate a change of management for Emotet, which has been run by the threat group TA542 and in April was ranked as the top malware threat - affecting six percent of companies worldwide.

Emotet, one of the most evasive and destructive malware delivery systems, caused substantial damage during its initial reign. After a coordinated takedown by authorities in early 2021, Emotet has reemerged as a global threat that will persist for organizations.

The Emotet malware operation is again spamming malicious emails after almost a four-month "Vacation" that saw little activity from the notorious cybercrime operation. Emotet is a malware infection distributed through phishing campaigns containing malicious Excel or Word documents.

The Emotet malware operation is again spamming malicious emails after almost a five-month "Vacation" that saw little activity from the notorious cybercrime operation.Emotet is a malware infection distributed through phishing campaigns containing malicious Excel or Word documents.
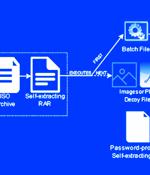
The notorious Emotet botnet has been linked to a new wave of malspam campaigns that take advantage of password-protected archive files to drop CoinMiner and Quasar RAT on compromised systems. In an attack chain detected by Trustwave SpiderLabs researchers, an invoice-themed ZIP file lure was found to contain a nested self-extracting archive, the first archive acting as a conduit to launch the second.

Threat actors associated with the notorious Emotet malware are continually shifting their tactics and command-and-control infrastructure to escape detection, according to new research from VMware. "The ongoing adaptation of Emotet's execution chain is one reason the malware has been successful for so long," researchers from VMware's Threat Analysis Unit said in a report shared with The Hacker News.

The Emotet malware is now being leveraged by ransomware-as-a-service groups, including Quantum and BlackCat, after Conti's official retirement from the threat landscape this year. Emotet started off as a banking trojan in 2014, but updates added to it over time have transformed the malware into a highly potent threat that's capable of downloading other payloads onto the victim's machine, which would allow the attacker to control it remotely.

While monitoring the Emotet botnet's current activity, security researchers found that the Quantum and BlackCat ransomware gangs are now using the malware to deploy their payloads. "The Emotet botnet has fueled major cybercriminal groups as an initial attack vector, or precursor, for numerous ongoing attacks," security researchers at intelligence company AdvIntel said.

The "New and improved" version of Emotet is exhibiting a "Troubling" behavior of effectively collecting and using stolen credentials, "Which are then being weaponized to further distribute the Emotet binaries," Charles Everette from Deep Instinct revealed in a blog post this week. In April, Emotet malware attacks returned after a 10-month "Spring break" with targeted phishing attacks linked to the threat actor known as TA542, which since 2014 has leveraged the Emotet malware with great success, according to a report by Proofpoint.