Security News

The malicious PoorTry kernel-mode Windows driver used by multiple ransomware gangs to turn off Endpoint Detection and Response (EDR) solutions has evolved into an EDR wiper, deleting files crucial...

In brief Malware that kills endpoint detection and response software has been spotted on the scene and, given it's deploying RansomHub, it could soon be prolific. A look inside the malware indicates it's not as dangerous as it appears at first glance, provided proper precautions are taken.

A cybercrime group with links to the RansomHub ransomware has been observed using a new tool designed to terminate endpoint detection and response software on compromised hosts, joining the likes of other similar programs like AuKill and Terminator. The EDR-killing utility has been dubbed EDRKillShifter by cybersecurity company Sophos, which discovered the tool in connection with a failed ransomware attack in May 2024.

Prolific Russian cybercrime syndicate FIN7 is using various pseudonyms to sell its custom security solution-disabling malware to different ransomware gangs. AvNeutralizer malware was previously thought to be solely linked to the Black Basta group, but fresh research has uncovered various underground forum listings of the malicious software now believed to be created by FIN7 operatives.

The cybercrime-focused enterprise known as FIN7 has come up with yet another trick to assure the effectiveness of its "EDR killer" tool, dubbed AvNeutralizer by researchers. They spotted the tool being offered for sale on underground forums by several sellers/personas, which they suspect to be part of the FIN7 cluster.

The notorious FIN7 hacking group has been spotted selling its custom "AvNeutralizer" tool, used to evade detection by killing enterprise endpoint protection software on corporate networks. The same threat actors are also likely tied to the BlackCat ransomware operation, which recently conducted an exit scam after stealing a UnitedHealth ransom payment.

SentinelOne and Palo Alto are two of the top brands in this space, and this comparison will help you decide if either one of the company's tools is right for you. While you can request a demo of Cortex XDR on Palo Alto's official website, there is no explicit price list of both Cortex XDR tiers as of May 2024.
Cybersecurity researchers have discovered a new cryptojacking campaign that employs vulnerable drivers to disable known security solutions (EDRs) and thwart detection in what's called a Bring...

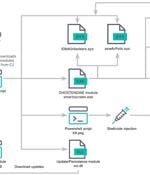
A malicious crypto mining campaign codenamed 'REF4578,' has been discovered deploying a malicious payload named GhostEngine that uses vulnerable drivers to turn off security products and deploy an XMRig miner. Researchers at Elastic Security Labs and Antiy have underlined the unusual sophistication of these crypto-mining attacks in separate reports and shared detection rules to help defenders identify and stop them.

A guide to finding the right endpoint detection and response (EDR) solution for your business’ unique needs. Cybersecurity has become an ongoing battle between hackers and small- and mid-sized...