Security News

The set of seven flaws are comprised of buffer overflow issues and flaws allowing for DNS cache-poisoning attacks. If exploited, these flaws could be chained together to allow remote code execution, denial of service and other attacks.

Seven vulnerabilities affecting Dnsmasq, a caching DNS and DHCP server used in a variety of networking devices and Linux distributions, could be leveraged to mount DNS cache poisoning attack and/or to compromise vulnerable devices. "Some of the bigger users of Dnsmasq are Android/Google, Comcast, Cisco, Red Hat, Netgear, and Ubiquiti, but there are many more. All major Linux distributions offer Dnsmasq as a package, but some use it more than others, e.g., in OpenWRT it is used a lot, Red Hat use it as part of their virtualization platforms, Google uses it for Android hotspots, while, for example Ubuntu just has it as an optional package," Shlomi Oberman, CEO and researcher at JSOF, told Help Net Security.

Israel-based security consultancy firm JSOF disclosed today seven Dnsmasq vulnerabilities, collectively known as DNSpooq, that can be exploited to launch DNS cache poisoning, remote code execution, and denial-of-service attacks against millions of affected devices. Three of the DNSpooq vulnerabilities allow for both DNS cache poisoning attacks.
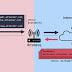
Dnsmasq, short for DNS masquerade, is a lightweight software with DNS forwarding capabilities used for locally caching DNS records, thus reducing the load on upstream nameservers and improving performance. If the malicious answer with the right transaction ID from the attacker arrives before the response from the authoritative server, then the DNS cache would be effectively poisoned, returning the attacker's chosen IP address instead of the legitimate address for as long as the DNS response was valid.
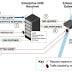
The U.S. National Security Agency on Friday said DNS over HTTPS - if configured appropriately in enterprise environments - can help prevent "Numerous" initial access, command-and-control, and exfiltration techniques used by threat actors. "DNS over Hypertext Transfer Protocol over Transport Layer Security, often referred to as DNS over HTTPS, encrypts DNS requests by using HTTPS to provide privacy, integrity, and 'last mile' source authentication with a client's DNS resolver," according to the NSA's new guidance.

The National Security Agency on Wednesday published guidance for businesses on the adoption of an encrypted domain name system protocol, specifically DNS over HTTPS. Designed to translate the domain names included in URLs into IP addresses, for an easier navigation of the Internet, DNS has become a popular attack vector, mainly because requests and responses are transmitted in plaintext. "Using DoH with external resolvers can be good for home or mobile users and networks that do not use DNS security controls. For enterprise networks NSA recommends using only designated enterprise DNS resolvers in order to properly leverage essential enterprise cybersecurity defenses, facilitate access to local network resources, and protect internal network information," the NSA notes.

The US National Security Agency says that companies should avoid using third party DNS resolvers to block threat actors' DNS traffic eavesdropping and manipulation attempts and to block access to internal network information. NSA's recommendation was made in a new advisory on the benefits of using DNS over HTTPS in enterprise environments, an encrypted domain name system protocol that blocks unauthorized access to the DNS traffic between clients and DNS resolvers.

Allot announced that a new mass-market cybersecurity solution, Allot DNS Secure, will join the Allot Secure family of cybersecurity solutions for communication service providers. The new solution is supported by an agreement with Open-Xchange to license its OX PowerDNS technology, which will be integrated into Allot DNS Secure.

This new protocol, called Oblivious DNS-over-HTTPS, hides the websites you visit from your ISP. Here's how it works: ODoH wraps a layer of encryption around the DNS query and passes it through a proxy server, which acts as a go-between the internet user and the website they want to visit. Because the DNS query is encrypted, the proxy can't see what's inside, but acts as a shield to prevent the DNS resolver from seeing who sent the query to begin with.

Microsoft issued guidance on how to mitigate a DNS cache poisoning vulnerability reported by security researchers from the University of California and Tsinghua University. Successfully exploiting the vulnerability could allow attackers to use modified DNS records to redirect a target to a malicious website under their control as part of DNS spoofing attacks.