Security News
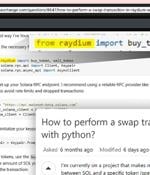
In yet another sign that threat actors are always looking out for new ways to trick users into downloading malware, it has come to light that the question-and-answer platform known as Stack Exchange has been abused to direct unsuspecting developers to bogus Python packages capable of draining their cryptocurrency wallets. The packages have been collectively downloaded 2,082 times.
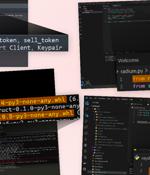
The threat actors behind an ongoing malware campaign targeting software developers have demonstrated new malware and tactics, expanding their focus to include Windows, Linux, and macOS systems. DEV#POPPER is the moniker assigned to an active malware campaign that tricks software developers into downloading booby-trapped software hosted on GitHub under the guise of a job interview.

Let's face it: AppSec and developers often feel like they're on opposing teams. Ever wish they proactively cared about security? The answer lies in a proven, but often overlooked, strategy: Security Champion Programs - a way to turn developers from adversaries into security advocates?

By scanning the most popular 100 organizations on GitHub, which collectively includes more than 50,000 publicly accessible repositories, researchers found active secrets from open source organizations and enterprises such as Cisco and Mozilla providing access to sensitive data and software. The exposed secrets could lead to significant financial losses, reputational damage, and legal consequences.

Cybersecurity researchers have discovered a malicious Python package uploaded to the Python Package Index (PyPI) repository that's designed to deliver an information stealer called Lumma (aka...

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.
An ongoing social engineering campaign is targeting software developers with bogus npm packages under the guise of a job interview to trick them into downloading a Python backdoor. Cybersecurity...

A new campaign tracked as "Dev Popper" is targeting software developers with fake job interviews in an attempt to trick them into installing a Python remote access trojan. The developers are asked to perform tasks supposedly related to the interview, like downloading and running code from GitHub, in an effort to make the entire process appear legitimate.
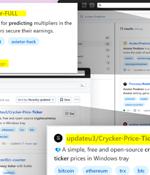
Threat actors are now taking advantage of GitHub's search functionality to trick unsuspecting users looking for popular repositories into downloading spurious counterparts that serve malware. The...

Google has filed a lawsuit against two app developers for engaging in an "international online consumer investment fraud scheme" that tricked users into downloading bogus Android apps from the...