Security News

Classification compliance? Records retention requirements? How quaint A US Department of Defense watchdog has opened an investigation into its own Secretary of Defense, Pete Hegseth, over his use...

The rules have changed. Again. Artificial intelligence is bringing powerful new tools to businesses. But it's also giving cybercriminals smarter ways to attack. They’re moving quicker, targeting...

If you do business in the United States, especially across state lines, you probably know how difficult it is to comply with U.S. state data privacy laws. The federal government and many U.S....

MORSE to pay -- .. .-.. .-.. .. --- -. ... for failing to meet cyber-grade A US defense contractor will cough up $4.6 million to settle complaints it failed to meet cybersecurity requirements on...

So much for that vacation A US Department of Defense electrical engineer has turned his world upside down after printing 155 pages from 20 documents, all of which were marked top secret and...

How to avoid another SolarWinds, Log4j, and XZ Utils situation Organizations concerned about software supply chain attacks should focus on role-based access control, system monitoring, and...
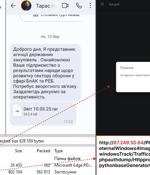
The Computer Emergency Response Team of Ukraine (CERT-UA) is warning of a new campaign that targets the defense sectors with Dark Crystal RAT (aka DCRat). The campaign, detected earlier this...

Data Theft Drove 94% of Global Cyberattacks in 2024 & Ransomware Defenses are “Increasingly Complex”
Ransomware groups now steal, encrypt, and threaten to leak company data on the dark web, forcing victims to pay or risk exposing sensitive information.

Ransomware doesn’t hit all at once—it slowly floods your defenses in stages. Like a ship subsumed with water, the attack starts quietly, below the surface, with subtle warning signs that are easy...

Think government cybersecurity is bad? Guess again. It’s alarmingly so The UK government is significantly behind on its 2022 target to harden systems against cyberattacks by 2025, with a new...