Security News

The U.K.'s National Crime Agency revealed today that they created multiple fake DDoS-for-hire service websites to identify cybercriminals who utilize these platforms to attack organizations. NCA says several thousands of people accessed its fake sites, which had a realistic appearance as a genuine booter service.

Poorly managed Linux SSH servers are being targeted as part of a new campaign that deploys different variants of malware called ShellBot. ShellBot is installed on servers that have weak credentials, but only after threat actors make use of scanner malware to identify systems that have SSH port 22 open.

A new malware botnet was discovered targeting Realtek SDK, Huawei routers, and Hadoop YARN servers to recruit devices into DDoS swarm with the potential for massive attacks. Akamai's analysts created a C2 of their own and interacted with simulated infections to stage HinataBot for DDoS attacks to observe the malware in action and infer its attack capabilities.
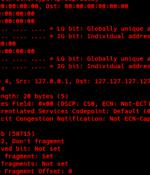
A new Golang-based botnet dubbed HinataBot has been observed to leverage known flaws to compromise routers and servers and use them to stage distributed denial-of-service attacks. The threat actors behind HinataBot are said to have been active since at least December 2022, with the attacks first attempting to use a generic Go-based Mirai variant before switching to their own custom malware starting from January 11, 2023.

Akamai reports having mitigated the largest DDoS attack ever launched against a customer based in the Asia-Pacific region. DDoS is an attack that involves sending a large volume of garbage requests to a targeted server, depleting its capacity, and thus rendering the websites, applications, or other online services it hosts unreachable by legitimate users.

After your incoming traffic has been scanned, all safe traffic is forwarded to your network or servers for processing through the GRE tunnel. GRE tunnels can transport or forward multicast traffic, which is essential for actions like routing protocol advertisement and for video conferencing applications, while a VPN can only transport unicast traffic.
A series of distributed-denial-of-service attacks shut down nine Danish hospitals' websites for a few hours on Sunday, but did not have any life-threatening impact on the medical centers' operations or digital infrastructure. "Region H the hospitals' websites are down," it read, in Danish.

At the beginning of January, Gcore faced an incident involving several L3/L4 DDoS attacks with a peak volume of 650 Gbps. Attackers exploited over 2000 servers belonging to one of the top three cloud providers worldwide and targeted a client who was using a free CDN plan. This value is comparable to the record DDoS attack on the largest Minecraft server, only one-fourth as massive.

A new Mirai botnet variant tracked as 'V3G4' targets 13 vulnerabilities in Linux-based servers and IoT devices to use in DDoS attacks. The malware spreads by brute-forcing weak or default telnet/SSH credentials and exploiting hardcoded flaws to perform remote code execution on the target devices.

"Over the past year, we've seen more attacks originate from cloud computing providers, Cloudflare researchers wrote in a report, adding that the network traffic used in the attacks over the weekend came from"numerous cloud providers. Given the increasing number of DDoS attacks coming from cloud providers, Cloudflare is trialing - what convenient timing - a free botnet threat feed to monitor attacks.