Security News

A U.K. national responsible for his role as the administrator of the now-defunct iSpoof online phone number spoofing service has been sentenced to 13 years and 4 months in prison. He pleaded guilty last month to a number of cyber offenses, including facilitating fraud and possessing and transferring criminal property.

Trend Micro has not elaborated on how Lemon Group infects devices with the malicious firmware containing Guerilla but clarified that the devices its analysts examined had been re-flashed with new ROMs. The analysts identified over 50 different ROMs infected with initial malware loaders, targeting various Android device vendors. "The criminal group has infected millions of android devices, mainly mobile phones, but also smart watches, smart TVs and more," reads the description of Trend Micro's Black Hat talk.
A cybercrime enterprise known as Lemon Group is leveraging millions of pre-infected Android smartphones worldwide to carry out their malicious operations, posing significant supply chain risks. The activity encompasses no fewer than 8.9 million compromised Android devices, particularly budget phones, with a majority of the infections discovered in the U.S., Mexico, Indonesia, Thailand, Russia, South Africa, India, Angola, the Philippines, and Argentina.

Infostealer malware, which consist of code that infects devices without the user's knowledge and steals data, remains widely available to buy through underground forums and marketplaces, with the volume of logs, or collections of stolen data, available for sale increasing at alarming rates, according to Secureworks. "Infostealers are a natural choice for cybercriminals who are looking to rapidly gain access to businesses and then monetize that access," said Don Smith, VP threat research, Secureworks CTU. "They are readily available for purchase, and within as little as 60 seconds of installation on an infected computer will immediately generate a return on investment in the form of stolen credentials and other sensitive information. However, what has really changed the game, as far as infostealers are concerned, is improvements in the various ways that criminals use to trick users into installing them. That, coupled with the development of dedicated marketplaces for the sale and purchase of this stolen data, has really upped the ante," added Smith.

The National Police of Spain said it arrested 40 individuals for their alleged involvement in an organized crime gang called Trinitarians. Among those apprehended include two hackers who carried out bank scams through phishing and smishing techniques and 15 other members of the crime syndicate, who have all been charged with a number of offenses such as bank fraud, forging documents, identity theft, and money laundering.

EFF has a good explainer on the problems with the new UN Cybercrime Treaty, currently being negotiated in Vienna. The draft treaty has the potential to rewrite criminal laws around the world, possibly adding over 30 criminal offenses and new expansive police powers for both domestic and international criminal investigations.
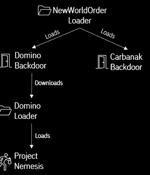
A new strain of malware developed by threat actors likely affiliated with the FIN7 cybercrime group has been put to use by the members of the now-defunct Conti ransomware gang, indicating collaboration between the two crews. The latest intrusion wave, spotted by IBM Security X-Force two months ago, involves the use of Dave Loader, a crypter previously attributed to the Conti group, to deploy the Domino backdoor.

The UN Cybercrime Treaty, to the extent it gets adopted, is expected to define global norms for lawful surveillance and legal processes available to investigate and prosecute cybercriminals. What concerns Rodriguez and other representatives of advocacy groups at the briefing is that the treaty negotiators will compromise on surveillance, privacy, and human rights.
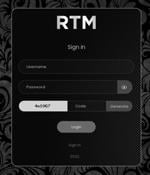
"The 'Read The Manual' Locker gang uses affiliates to ransom victims, all of whom are forced to abide by the gang's strict rules," cybersecurity firm Trellix said in a report shared with The Hacker News. Attack chains mounted by the group have since evolved to deploy a ransomware payload on compromised hosts.

"Account access credentials advertised for sale on Genesis Market included those connected to the financial sector, critical infrastructure, and federal, state, and local government agencies," the U.S. Department of Justice said in a statement. DoJ called Genesis Market one of the "Most prolific initial access brokers in the cybercrime world."