Security News

The 8220 gang has been leveraging an old Oracle WebLogic Server vulnerability to distribute malware, the Imperva Threat Research team has found. Active since 2017, the 8220 gang has been known for deploying cryptocurrency miners on Linux and Windows hosts by exploiting known vulnerabilities.

A new set of 16 malicious NPM packages are pretending to be internet speed testers but are, in reality, coinminers that hijack the compromised computer's resources to mine cryptocurrency for the threat actors. The packages were uploaded onto NPM, an online repository containing over 2.2 million open-source JavaScript packages shared among software developers to speed up the coding process.

A new Linux malware downloader created using SHC has been spotted in the wild, infecting systems with Monero cryptocurrency miners and DDoS IRC bots. According to ASEC researchers, who discovered the attack, the SHC loader was uploaded to VirusTotal by Korean users, with attacks generally focused on Linux systems in the same country.

A now-patched vulnerability in VMware Workspace ONE Access has been observed being exploited to deliver both cryptocurrency miners and ransomware on affected machines. "The attacker intends to utilize a victim's resources as much as possible, not only to install RAR1Ransom for extortion, but also to spread GuardMiner to collect cryptocurrency," Fortinet FortiGuard Labs researcher Cara Lin said in a Thursday report.

Security researchers estimate that the financial impact of cryptominers infecting cloud servers costs victims about $53 for every $1 worth of cryptocurrency threat actors mine on hijacked devices. The threat actors load modified OS images containing XMRig, a miner for Monero, which is a privacy-oriented hard-to-trace cryptocurrency, and currently the most profitable CPU-based mining.
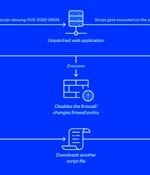
A now-patched critical security flaw affecting Atlassian Confluence Server that came to light a few months ago is being actively exploited for illicit cryptocurrency mining on unpatched installations. In one of the infection chains observed by the cybersecurity company, the flaw was leveraged to download and run a shell script on the victim's machine, which, in turn, fetched a second shell script.

AT&T cybersecurity researchers have discovered a sneaky piece of malware targeting Linux endpoints and IoT devices in the hopes of gaining persistent access and turning victims into crypto-mining drones. Popular adventure clothing brand The North Face and shoe company Vans, subsidiaries of the same parent company, have admitted to a credential stuffing attack that netted its attacker 194,905 user's worth of PII. Most every piece of PII stored on the two websites were compromised, with the exception of credit card numbers, which the brands' parent company VF Outdoors said it doesn't store on its sites.

As many as three disparate but related campaigns between March and Jun 2022 have been found to deliver a variety of malware, including ModernLoader, RedLine Stealer, and cryptocurrency miners onto compromised systems. "The actors use PowerShell,.NET assemblies, and HTA and VBS files to spread across a targeted network, eventually dropping other pieces of malware, such as the SystemBC trojan and DCRat, to enable various stages of their operations," Cisco Talos researcher Vanja Svajcer said in a report shared with The Hacker News.
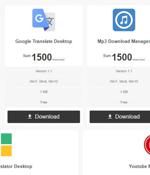
The campaign entails serving malware through free software hosted on popular sites such as Softpedia and Uptodown. In an interesting tactic, the malware puts off its execution for weeks and separates its malicious activity from the downloaded fake software to avoid detection.
Threat actors have begun to use the Tox peer-to-peer instant messaging service as a command-and-control method, marking a shift from its earlier role as a contact method for ransomware negotiations. The findings from Uptycs, which analyzed an Executable and Linkable Format artifact that functions as a bot and can run scripts on the compromised host using the Tox protocol.