Security News

Cybersecurity researchers have shed light on an "auto-propagating" cryptocurrency mining botnet called Outlaw (aka Dota) that's known for targeting SSH servers with weak credentials. "Outlaw is a...

Cryptojacking may be stealthy, but its impact is anything but. From inflated cloud bills to sluggish performance, it's a threat that companies can't ignore. Learn more from Pentera about how...

Google on Wednesday shed light on a financially motivated threat actor named TRIPLESTRENGTH for its opportunistic targeting of cloud environments for cryptojacking and on-premise ransomware...

This is what happens when you publish PoCs immediately, hm? "Several cloud deployments" are already compromised following the disclosure of the maximum-severity vulnerability in Aviatrix...

A Nebraska man pleaded guilty on Thursday to operating a large-scale cryptojacking operation after being arrested and charged in April. [...]

A Nebraska man pleaded guilty on Thursday to operating a large-scale cryptojacking operation after being arrested and charged in April. [...]

Cybersecurity researchers have uncovered a new cryptojacking campaign targeting the Docker Engine API with the goal of co-opting the instances to join a malicious Docker Swarm controlled by the...

The cryptojacking operation known as TeamTNT has likely resurfaced as part of a new campaign targeting Virtual Private Server (VPS) infrastructures based on the CentOS operating system. "The...
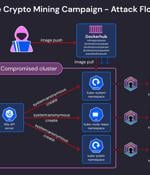
Cybersecurity researchers have warned of an ongoing cryptojacking campaign targeting misconfigured Kubernetes clusters to mine Dero cryptocurrency. Cloud security firm Wiz, which shed light on the...

The threat actor known as Commando Cat has been linked to an ongoing cryptojacking attack campaign that leverages poorly secured Docker instances to deploy cryptocurrency miners for financial...