Security News

The U.S. Justice Department on Tuesday announced the arrest of a married couple in connection with conspiring to launder cryptocurrency worth $4.5 billion that was siphoned during the hack of the virtual currency exchange Bitfinex in 2016. Ilya Lichtenstein, 34, and his wife, Heather Morgan, 31, both of New York, are alleged to have "Stolen funds through a labyrinth of cryptocurrency transactions," with the law enforcement getting hold of over $3.6 billion in cryptocurrency by following the money trails, resulting in the "Largest financial seizure ever."

Hackers have exploited a vulnerability in the Wormhole cross-chain crypto platform to steal $326 million in cryptocurrency. Wormhole is a platform that allows users to transfer cryptocurrency across different blockchains.

Experian released its annual forecast, which reveals five fraud threats for the new year. With consumers continuing to take a digital-first approach to everything from shopping, dating and investing, fraudsters are finding new and innovative ways to commit fraud.
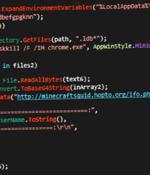
A new evasive crypto wallet stealer named BHUNT has been spotted in the wild with the goal of financial gain, adding to a list of digital currency stealing malware such as CryptBot, Redline Stealer, and WeSteal. "BHUNT is a modular stealer written in.NET, capable of exfiltrating wallet contents, passwords stored in the browser, and passphrases captured from the clipboard," Bitdefender researcher said in a technical report on Wednesday.

Russia has floated the prospect of Putin a ban on cryptocurrencies. The Bank of Russia, the nation's central bank, yesterday published a Consultation Paper [PDF] titled "Cryptocurrencies: Trends, Risks, and Regulation" that ponders the impact of unbacked cryptocurrencies and stablecoins on Russia's economy.

The global cryptocurrency market is expected to grow from $1.44 billion in 2020 to $1.63 billion in 2021 at a compound annual growth rate of 12.9%. The market is expected to reach $2.73 billion in 2025 at a CAGR of 13.8%, according to ResearchAndMarkets. The cryptocurrency market consists of sales of digital or virtual currencies by entities that operate independently of a central bank and employ encryption techniques to regulate the formation of their units and verify the transfer of payments.

Thieves operating for the North Korean government made off with almost $400m in digicash last year in a concerted attack to steal and launder as much currency as they could. Bitcoin used to be a top target but Ether is now the most stolen currency, say the researchers, accounting for 58 per cent of the funds filched.

Operators associated with the Lazarus sub-group BlueNoroff have been linked to a series of cyberattacks targeting small and medium-sized companies worldwide with an aim to drain their cryptocurrency funds, in what's yet another financially motivated operation mounted by the prolific North Korean state-sponsored actor. Russian cybersecurity company Kaspersky, which is tracking the intrusions under the name "SnatchCrypto," noted that the campaign has been running since at 2017, adding the attacks are aimed at startups in the FinTech sector located in China, Hong Kong, India, Poland, Russia, Singapore, Slovenia, the Czech Republic, the U.A.E., the U.S., Ukraine, and Vietnam.

Cybersecurity software company NortonLifeLock is coming under fire for its decision late last year to begin installing Ethereum mining software on its Norton 360 customers' PCs without their permission or knowledge. Norton Crypto, the new Norton 360 mining component, isn't enabled without the user opting in, but that hasn't stopped users from taking to Norton's Crypto forum to register their discontent, and they aren't all upset about the sneaky installation.

Cryptocurrency users in Ethiopia, Nigeria, India, Guatemala, and the Philippines are being targeted by a new variant of the Phorpiex botnet called Twizt that has resulted in the theft of virtual coins amounting to $500,000 over the last one year. Israeli security firm Check Point Research, which detailed the attacks, said the latest evolutionary version "Enables the botnet to operate successfully without active servers," adding it supports no less than 35 wallets associated with different blockchains, including Bitcoin, Ethereum, Dash, Dogecoin, Litecoin, Monero, Ripple, and Zilliqa, to facilitate crypto theft.