Security News

Even after years of warnings, changing password requirements, and multiple forms of authentication, password stealing remains a top attack method used by cyber criminals. The latest report from the Ponemon Institute shares that 54% of security incidents were caused by credential theft, followed by ransomware and DDoS attacks.

Abnormal Security released a which report explores the current email threat landscape and provides insight into the latest advanced email attack trends, including increases in business email compromise, the evolution of financial supply chain compromise and the rise of brand impersonation in credential phishing attacks. The research found a 48% increase in email attacks over the previous six months, and 68.5% of those attacks included a credential phishing link.

How credential phishing attacks threaten a host of industries and organizations. A report released Thursday by email security provider Abnormal Security looks at the latest wave of credential phishing attacks and offers advice on how to stop them.

60% of IT security decision makers believe their overall security strategy does not keep pace with the threat landscape, and that they are either lagging behind, treading water, or merely running to keep up, according to a survey by Sapio Research. This Help Net Security video uncovers why companies have a long way to go to protect privileged identities and access.
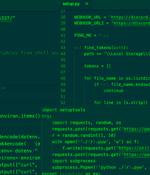
In what's yet another instance of malicious packages creeping into public code repositories, 10 modules have been removed from the Python Package Index for their ability to harvest critical data points such as passwords and Api tokens. The packages "Install info-stealers that enable attackers to steal developer's private data and personal credentials," Israeli cybersecurity firm Check Point said in a Monday report.

Threat analysts have discovered ten malicious Python packages on the PyPI repository, used to infect developer's systems with password-stealing malware. The fake packages used typosquatting to impersonate popular software projects and trick PyPI users into downloading them.

The U.S. Cybersecurity and Infrastructure Security Agency on Friday added the recently disclosed Atlassian security flaw to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation. The vulnerability, tracked as CVE-2022-26138, concerns the use of hard-coded credentials when the Questions For Confluence app is enabled in Confluence Server and Data Center instances.

Atlassian has patched a critical hardcoded credentials vulnerability in Confluence Server and Data Center that could let remote, unauthenticated attackers log into vulnerable, unpatched servers. According to Atlassian, the app helps improve communication with the organization's internal Q&A team and is currently installed on over 8,000 Confluence servers.

Train for some of today's top cybersecurity credentials for $39 We may be compensated by vendors who appear on this page through methods such as affiliate links or sponsored partnerships. There's significant demand for ethical hackers and cybersecurity expertise across industries.

Sonatype researchers have discovered Python packages that contain malicious code that peek into and expose secret AWS credentials, network interface information, and environment variables. All those credentials and metadata then get uploaded to one or more endpoints, and anyone on the web can see this.