Security News
The notorious Conti ransomware gang, which last month staged an attack on Costa Rican administrative systems, has threatened to "Overthrow" the new government of the country. "We are determined to overthrow the government by means of a cyber attack, we have already shown you all the strength and power," the group said on its official website.

Costa Rican President Rodrigo Chaves declared a state of national cybersecurity emergency over the weekend following a financially motivated Conti ransomware attack against his administration that has hamstrung the government and economy of the Latin American nation. The attack-attributed to the prolific Conti ransomware group-occurred three weeks ago not long after Chaves took office; in fact, the state of emergency was one of his first decrees as president.

The US government is offering up to $15 million for information about key leaders of the notorious Conti ransomware group and any individual participating in an attack using a variant of Conti's malware. In its notice issued May 6, the US Department of State said the Conti ransomware variant was the costliest strain of ransomware on record, noting that as of January, there were more than 1,000 victims of attack that involved Conti ransomware, with payouts surpassing $150 million.

The Costa Rican President Rodrigo Chaves has declared a national emergency following cyber attacks from Conti ransomware group on multiple government bodies.On Sunday, May 8th, the newly elected Costa Rican President Chaves declared a national emergency citing ongoing Conti ransomware attacks as the reason.

The U.S. State Department has announced rewards of up to $10 million for any information leading to the identification of key individuals who are part of the infamous Conti cybercrime gang. It's offering another $5 million for intelligence information that could help arrest or convict individuals who are conspiring or attempting to affiliate with the group in a ransomware attack.

The US Department of State is offering up to $15 million for information that helps identify and locate leadership and co-conspirators of the infamous Conti ransomware gang. Up to $10 million of this reward are offered for info on Conti leaders' identity and location, and an additional $5 million for leading to the arrest and/or convictions of individuals who conspired or attempted to participate in Conti ransomware attacks.

The US Department of State is offering up to $15 million for information that helps identify and locate leadership and co-conspirators of the infamous Conti ransomware gang. Up to $10 million of this reward are offered for info on Conti leaders' identity and location, and an additional $5 million for leading to the arrest and/or convictions of individuals who conspired or attempted to participate in Conti ransomware attacks.

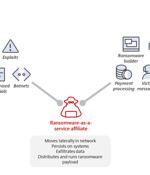
An analysis of four months of chat logs spanning more than 40 conversations between the operators of Conti and Hive ransomware and their victims has offered an insight into the groups' inner workings and their negotiation techniques. Conti and Hive are among the most prevalent ransomware strains in the threat landscape, cumulatively accounting for 29.1% of attacks detected during the three-month-period between October and December 2021.

A sophisticated malware loader dubbed Bumblebee is being used by at least three cybercriminal groups that have links to ransomware gangs, according to cybersecurity researchers. Researchers with both Proofpoint and Cybereason found code similarities between Bumblebee and TrickBot's malware.

A newly discovered malware loader called Bumblebee is likely the latest development of the Conti syndicate, designed to replace the BazarLoader backdoor used to deliver ransomware payloads. The emergence of Bumblebee in phishing campaigns in March coincides with a drop in using BazarLoader for delivering file-encrypting malware, researchers say.