Security News

Details have emerged on how more than a billion personal records were stolen in China and put up for sale on the dark web, and it all boils down to a unprotected online dashboard that left the data open to anyone who could find it. The data collection included names, addresses, birthplaces, national ID numbers, cellphone numbers, and details of any related police records.

A prominent Chinese tech CEO has cited human error as the likely reason hackers got their hands on the personal data of 1 billion people in China from a Shanghai police database and then put some of it up for sale on illicit online markets. An annual report on data breaches by Verizon-the 2022 Data Breach Investigations Report-cited the "Human element" as responsible for 82 percent of the breaches analyzed by researchers, with 13 percent directly attributed to human error.

A group of politicians and lawmakers in the UK have backed a campaign to ban the sale of CCTV systems made by companies alleged to introduce potential security issues as well as being linked to human rights abuses in China. Organized by campaign group Big Brother Watch, the letter said that partly Chinese state-owned CCTV manufacturers Hikvision and Dahua should be banned from sale or use in the UK. Both manufacturers are banned from trading in the US, owing both to security concerns and alleged evidence of their use in so-called "Re-education" camps in Xinjiang, where China is accused of detaining an estimated 1 million Uyghurs and subjecting them to abuse, torture, and forced sterilization, the campaigners said.

A threat actor has taken to a forum for news and discussion of data breaches with an offer to sell what they assert is a database containing records of over a billion Chinese civilians - allegedly stolen from the Shanghai Police. HackerDan released sample datasets: one containing delivery addresses and often instructions for drivers; another with police records; and the last with personal identification information like name, national ID number address, height, and gender.

An anonymous threat actor is selling several databases they claim to contain more than 22 terabytes of stolen information on roughly 1 billion Chinese citizens for 10 bitcoins. Based on the information they shared regarding the allegedly stolen data, the databases contain Chinese national residents' names, addresses, national ID numbers, contact info numbers, and several billion criminal records.

Following heightened worries that U.S. users' data had been accessed by TikTok engineers in China between September 2021 and January 2022, the company sought to assuage U.S. lawmakers that it's taking steps to "Strengthen data security." "Employees outside the U.S., including China-based employees, can have access to TikTok U.S. user data subject to a series of robust cybersecurity controls and authorization approval protocols overseen by our U.S.-based security team," TikTok CEO Shou Zi Chew wrote in the memo.
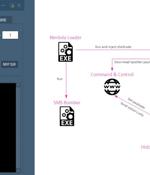
The novel loader, dubbed Nimbda, is "Bundled with a Chinese language greyware 'SMS Bomber' tool that is most likely illegally distributed in the Chinese-speaking web," Israeli cybersecurity company Check Point said in a report. "Whoever crafted the Nim loader took special care to give it the same executable icon as the SMS Bomber that it drops and executes," the researchers said.

Two Chinese hacking groups conducting cyber espionage and stealing intellectual property from Japanese and western companies are deploying ransomware as a decoy to cover up their malicious activities. Threat analysts from Secureworks say that the use of ransomware in espionage operations is done to obscure their tracks, make attribution harder, and create a powerful distraction for defenders.

Cybersecurity researchers have discovered a new campaign attributed to the Chinese "Tropic Trooper" hacking group, which employs a novel loader called Nimbda and a new variant of the Yahoyah trojan. The trojan is bundled in a greyware tool named 'SMS Bomber,' which is used for denial of service attacks against phones, flooding them with messages.
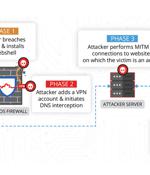
A sophisticated Chinese advanced persistent threat actor exploited a critical security vulnerability in Sophos' firewall product that came to light earlier this year to infiltrate an unnamed South Asian target as part of a highly-targeted attack. "The attacker implement[ed] an interesting web shell backdoor, create[d] a secondary form of persistence, and ultimately launch[ed] attacks against the customer's staff," Volexity said in a report.