Security News

Yesterday the CAC detailed some of the 12,000 acts of online fraud perpetrated against minors it handled this year. The unfortunate 15 year old, whom the CAC identified as Tan Moumou, was playing a mobile game when an unknown person added him as a friend on messaging platform WeChat and claimed he could circumvent China's gaming restrictions.

An extensive series of attacks detected in January used new Windows malware to backdoor government entities and organizations in the defense industry from several countries in Eastern Europe. Kaspersky linked the campaign with a Chinese APT group tracked as TA428, known for its information theft and espionage focus and attacking organizations in Asia and Eastern Europe [1, 2, 3, 4]. The threat actors successfully compromised the networks of dozens of targets, sometimes even taking control of their entire IT infrastructure by hijacking systems used to manage security solutions.

Researchers have disclosed a new offensive framework called Manjusaka that they call a "Chinese sibling of Sliver and Cobalt Strike." "A fully functional version of the command-and-control, written in GoLang with a User Interface in Simplified Chinese, is freely available and can generate new implants with custom configurations with ease, increasing the likelihood of wider adoption of this framework by malicious actors," Cisco Talos said in a new report.

Speaker of the US House of Representatives Nancy Pelosi has tied her controversial visit to Taiwan to an alleged barrage of China-directed cyber-attacks against the territory. The column details many Chinese acts that Pelosi alleges Taiwan has had to defend - including some in cyberspace, where she accused China of "Launching scores of attacks on Taiwan government agencies each day."

Researchers have observed a new post-exploitation attack framework used in the wild, named Manjusaka, which can be deployed as an alternative to the widely abused Cobalt Strike toolset or parallel to it for redundancy. Its RAT implants support command execution, file access, network reconnaissance, and more, so hackers can use it for the same operational goals as Cobalt Strike.

The popularity of stolen data bazaar BreachForums surged after it was used to sell a giant database of stolen information describing Chinese citizens, threat intelligence firm Cybersixgill said on Thursday. The number of leaks posted on BreachForums increased - from an average of 14 a month to 52 per month - following the posting of the infamous billion-record Shanghai National Police database in early July, reported Cybersixgill.
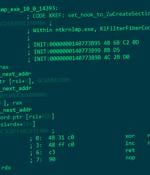
An unknown Chinese-speaking threat actor has been attributed to a new kind of sophisticated UEFI firmware rootkit called CosmicStrand. "The rootkit is located in the firmware images of Gigabyte or ASUS motherboards, and we noticed that all these images are related to designs using the H81 chipset," Kaspersky researchers said in a new report published today.

The government of Belgium has claimed it detected three Chinese Advanced Persistent Threat actors attacking its public service and defence forces. A government statement names Advanced Persistent Threat 27, 30, and 31 - aka UNSC 2814, GALLIUM, and SOFTCELL - as the groups responsible for the attacks.

The Minister for Foreign Affairs of Belgium says multiple Chinese state-backed threat groups targeted the country's defense and interior ministries. "Belgium assesses these malicious cyber activities to have been undertaken by Chinese Advanced Persistent Threats."

The US Federal Communications Commission notified Congress on Friday that the cost to rip and replace equipment kit from Huawei and ZTE installed at US telcos is more than $3 billion higher than funding allocated for the program. FCC chair Jessica Rosenworcel wrote to explain the situation, which arose from the USA's desire to remove Chinese comms kit at local carriers in the name of national security.