Security News

As the DigiCert drama continues, we now have a better idea of the size and scope of the problem - with the organization's infosec boss admitting the SSL/TLS certificate revocation sweep will affect tens of thousands of its customers, some of which have warned that the short notice may have real-world safety implications and disrupt critical services. A brief refresher on what happened: On July 29, the certificate authority said at least some customers had just 24 hours to replace their previously issued security certificates due to a five-year-old programming flaw in its systems.

DigiCert urges critical infrastructure operators to request a delay if they cannot reissue their certificates, as required by an ongoing certificate mass-revocation process announced on Tuesday. [...]

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

AnyDesk has copped to an IT security "Incident" in which criminals broke into the remote-desktop software maker's production systems. "We have revoked all security-related certificates and systems have been remediated or replaced where necessary," AnyDesk said.

The Computer Emergency Response Team of Ukraine (CERT-UA) has warned of a new phishing campaign orchestrated by the Russia-linked APT28 group to deploy previously undocumented malware such as...

India's government has granted its Computer Emergency Response Team, CERT-In, immunity from Right To Information requests - the nation's equivalent of the freedom of information queries in the US, UK, or Australia. Reasons for the exemption have not been explained, but The Register has reported on one case in which an RTI request embarrassed CERT-In. That case related to India's sudden decision, in April 2022, to require businesses of all sizes to report infosec incidents to CERT-in within six hours of detection.

The suspected man-in-the-middle attack was identified when the administrator of jabber. Ru, the largest Russian XMPP service, received a notification that one of the servers' certificates had expired.
The Computer Emergency Response Team of Ukraine (CERT-UA) has revealed that threat actors "interfered" with at least 11 telecommunication service providers in the country between May and September...
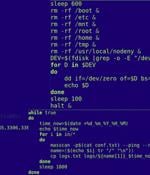
The Computer Emergency Response Team of Ukraine on Tuesday said it thwarted a cyber attack against an unnamed critical energy infrastructure facility in the country. "Visiting the link will download a ZIP archive containing three JPG images and a BAT file 'weblinks.cmd' to the victim's computer," CERT-UA said, attributing it to the Russian threat actor known as APT28.

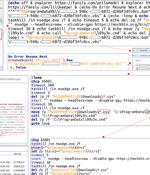
The Russia-linked threat actor known as Gamaredon has been observed conducting data exfiltration activities within an hour of the initial compromise. "As a vector of primary compromise, for the most part, emails and messages in messengers are used, in most cases, using previously compromised accounts," the Computer Emergency Response Team of Ukraine said in an analysis of the group published last week.