Security News

Cybersecurity researchers have disclosed details of an artificial intelligence (AI) powered platform called AkiraBot that's used to spam website chats, comment sections, and contact forms to...
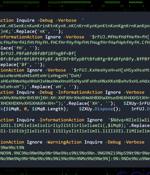
A new malware campaign has been observed leveraging social engineering tactics to deliver an open-source rootkit called r77. The activity, condemned OBSCURE#BAT by Securonix, enables threat actors...

Cybersecurity researchers have uncovered a widespread phishing campaign that uses fake CAPTCHA images shared via PDF documents hosted on Webflow's content delivery network (CDN) to deliver the...

A widespread phishing campaign has been observed leveraging bogus PDF documents hosted on the Webflow content delivery network (CDN) with an aim to steal credit card information and commit...
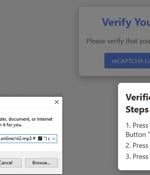
Cybersecurity researchers are calling attention to a new malware campaign that leverages fake CAPTCHA verification checks to deliver the infamous Lumma information stealer. "The campaign is...

Threat actors on X are exploiting the news around Ross Ulbricht to direct unsuspecting users to a Telegram channel that tricks them into executing PowerShell code that infects them with malware. [...]

As if the bot defense measure wasn't obnoxious enough Though the same couldn't be said for most of us mere mortals, Vercel CEO Guillermo Rauch had a productive festive period, resulting in a...

A large-scale malvertising campaign distributed the Lumma Stealer info-stealing malware through fake CAPTCHA verification pages that prompt users to run PowerShell commands to verify they are not...
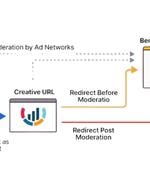
Cybersecurity researchers have shed light on a previously undocumented aspect associated with ClickFix-style attacks that hinge on taking advantage of a single ad network service as part of a...

This is really interesting. It’s a phishing attack targeting GitHub users, tricking them to solve a fake Captcha that actually runs a script that is copied to the command line. Clever.