Security News
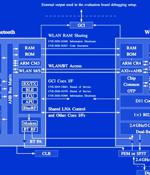
Cybersecurity researchers have demonstrated a new attack technique that makes it possible to leverage a device's Bluetooth component to directly extract network passwords and manipulate traffic on a Wi-Fi chip. The novel attacks work against the so-called "Combo chips," which are specialized chips that are equipped to handle different types of radio wave-based wireless communications, such as Wi-Fi, Bluetooth, and LTE. "We provide empirical evidence that coexistence, i.e., the coordination of cross-technology wireless transmissions, is an unexplored attack surface," a group of researchers from the Technical University of Darmstadt's Secure Mobile Networking Lab and the University of Brescia said in a new paper.

The vice president of the US, Kamala Harris, was mocked by commentators this week for her aversion to Bluetooth on security grounds. Security professionals think she has a point - given her position.

Researchers at the University of Darmstadt, Brescia, CNIT, and the Secure Mobile Networking Lab, have published a paper that proves it's possible to extract passwords and manipulate traffic on a WiFi chip by targeting a device's Bluetooth component. To exploit these vulnerabilities, the researchers first needed to perform code execution on either the Bluetooth or WiFi chip.

The embargo period is over for a proof-of-concept tool to test for the recently revealed BrakTooth flaws in Bluetooth devices, and the researchers who discovered them have released both the test kit and full exploit code for the bugs. BrakTooth is a collection of flaws affecting commercial Bluetooth stacks on more than 1,400 chipsets used in billions of devices - including smartphones, PCs, toys, internet-of-things devices and industrial equipment - that rely on Bluetooth Classic for communication.

Over the past few years, mobile devices have become increasingly chatty over the Bluetooth Low Energy protocol and this turns out to be a somewhat significant privacy risk. More recently, the US-based researchers explain, software for tracking COVID-19 has used mobile devices as BLE beacons, broadcasting signals in the service of public health.

Reg scribe spends week being watched by government Bluetooth wristband, emerges to more surveillance
Accompanying documentation explained that the gateway can measure distance to the wristband. Since the alternative was to serve the quarantine in a cramped and expensive hotel room with my kids, I was prepared to allow the app the access it wanted.

A Norwegian student who went wardriving around Oslo on a pushbike has discovered that several popular models of Bluetooth headphones don't implement MAC address randomisation - meaning they can be used to track their wearers. Norwegian state broadcaster NRK revealed Bjorn Hegnes' findings after helping him analyse Bluetooth emissions from a dozen different models of audio headphones, contained within 1.7 million Bluetooth messages he intercepted.

Vulnerabilities collectively referred to as BrakTooth are affecting Bluetooth stacks implemented on system-on-a-chip circuits from over a dozen vendors. Researchers from the Singapore University of Technology and Design have published details about BrakTooth - a new family of security vulnerabilities in commercial Bluetooth stacks.

A set of new security vulnerabilities has been disclosed in commercial Bluetooth stacks that could enable an adversary to execute arbitrary code and, worse, crash the devices via denial-of-service attacks. Collectively dubbed "BrakTooth", the 16 security weaknesses span across 13 Bluetooth chipsets from 11 vendors such as Intel, Qualcomm, Zhuhai Jieli Technology, and Texas Instruments, covering an estimated 1,400 or more commercial products, including laptops, smartphones, programmable logic controllers, and IoT devices.

Researchers have disclosed a group of 16 different vulnerabilities collectively dubbed BrakTooth, which impact billions of devices that rely on Bluetooth Classic for communication. Potentially, billions of devices could be affected worldwide, researchers said.