Security News

A malicious campaign focused on the industrial sector in the Middle East has been expanded to also target Mac computers, security researchers at Kaspersky have discovered. Dubbed WildPressure, the campaign started in May 2019 and for more than a year it involved only a Windows version of a malware named Milum.

Cisco's Talos security unit says it has detected an increased rate of attacks on targets on the Indian subcontinent and named an advanced persistent threat actor named SideCopy as the source. SideCopy's infrastructure, Talos opined, "Indicates a special interest in victims in Pakistan and India," as the malware used only initiates actions if it detects infections in those two countries.
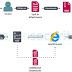
Cybersecurity researchers on Thursday took the wraps off a new, ongoing espionage campaign targeting corporate networks in Spanish-speaking countries, specifically Venezuela, to spy on its victims. Dubbed "Bandidos" by ESET owing to the use of an upgraded variant of Bandook malware, the primary targets of the threat actor are corporate networks in the South American country spanning across manufacturing, construction, healthcare, software services, and retail sectors.

Cybercriminals are already taking advantage of the ransomware attack against IT firm Kaseya to deploy spam designed to infect computers with Cobalt Strike-delivered malware. In a July 6 update to an ongoing blog and a tweet about the Kaseya incident, security firm Malwarebytes said that its Threat Intelligence team has detected a malicious spam campaign exploiting the Kaseya VSA attack.

Kaseya issued its annual IT operations report only three days before getting hit by a ransomware attack. According to an analysis by Sophos, the bad actors behind this attack "Not only found a new vulnerability in Kaseya's supply chain, but used a malware protection program as the delivery vehicle for the REvil ransomware code."

Administrators are urged to apply the latest patches from Microsoft and disable the Windows Print spooler service in domain controllers and systems not used for printing. Microsoft is grappling with a couple of security holes in its Windows Print spooler service that could allow attackers to remotely control an affected system.

Kaseya Denies Paying Cybercriminals Who Launched Ransomware Attack - Kaseya says it did not pay any money to the cybercriminals who recently launched a ransomware attack against the company's customers. Kaseya Obtains Universal Decryptor for Ransomware Attack Victims - Kaseya has obtained a universal decryptor that should allow victims of the recent ransomware attack to recover their files.

A utility that provides power in rural southeastern Alabama was hit by a ransomware attack that meant customers temporarily can't access their account information, but an executive said Tuesday that systems were beginning to be brought back online. Wiregrass Electric Cooperative, which serves about 25,000 members, did not pay a ransom and didn't have any data compromised in the attack, chief operating officer Brad Kimbro said.

U.S. technology firm Kaseya, which is firefighting the largest ever supply-chain ransomware strike on its VSA on-premises product, ruled out the possibility that its codebase was unauthorizedly tampered with to distribute malware. While initial reports raised speculations that REvil, the ransomware gang behind the attack, might have gained access to Kaseya's backend infrastructure and abused it to deploy a malicious update to VSA servers running on client premises, in a modus operandi similar to that of the devastating SolarWinds hack, it has since emerged that a never-before-seen security vulnerability in the software was leveraged to push ransomware to Kaseya's customers.

A ransomware attack against a single company's software product is having a ripple effect across more than 1,000 organizations. The supply chain nature of Kaseya's business means that far more companies have now been caught in the aftermath of the attack.