Security News > 2024 > July > Researchers Reveal ConfusedFunction Vulnerability in Google Cloud Platform
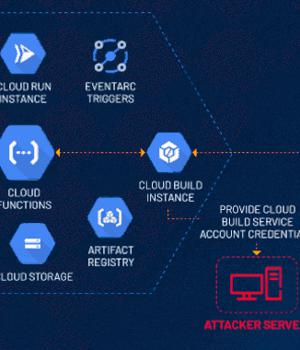
Cybersecurity researchers have disclosed a privilege escalation vulnerability impacting Google Cloud Platform's Cloud Functions service that an attacker could exploit to access other services and sensitive data in an unauthorized manner.
"An attacker could escalate their privileges to the Default Cloud Build Service Account and access numerous services such as Cloud Build, storage, artifact registry and container registry," the exposure management company said in a statement.
The problem discovered by Tenable has to do with the fact that a Cloud Build service account is created in the background and linked to a Cloud Build instance by default when a Cloud Function is created or updated.
This permission could then be abused to access other Google Cloud services that are also created in tandem with the Cloud Function, including Cloud Storage, Artifact Registry, and Container Registry.
"The ConfusedFunction vulnerability highlights the problematic scenarios that may arise due to software complexity and inter-service communication in a cloud provider's services," Tenable researcher Liv Matan said.
"While the GCP fix has reduced the severity of the problem for future deployments, it didn't completely eliminate it. That's because the deployment of a Cloud Function still triggers the creation of the aforementioned GCP services. As a result, users must still assign minimum but still relatively broad permissions to the Cloud Build service account as part of a function's deployment."
News URL
https://thehackernews.com/2024/07/experts-expose-confusedfunction.html
Related news
- Google Fixed Cloud Run Vulnerability Allowing Unauthorized Image Access via IAM Misuse (source)
- BlackLock Ransomware Exposed After Researchers Exploit Leak Site Vulnerability (source)
- Google Patches Quick Share Vulnerability Enabling Silent File Transfers Without Consent (source)
- Google's got a hot cloud infosec startup, a new unified platform — and its eye on Microsoft's $20B+ security biz (source)
- Researchers Identify Rack::Static Vulnerability Enabling Data Breaches in Ruby Servers (source)