Security News > 2024 > July > New Ransomware Group Exploiting Veeam Backup Software Vulnerability
A now-patched security flaw in Veeam Backup & Replication software is being exploited by a nascent ransomware operation known as EstateRansomware.
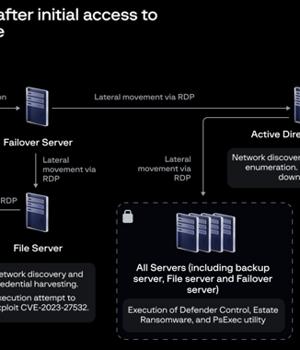
"Before the ransomware attack, there were VPN brute-force attempts noted in April 2024 using a dormant account identified as 'Acc1.' Several days later, a successful VPN login using 'Acc1' was traced back to the remote IP address 149.28.106[.]252.".
Group-IB said it observed the actor exploiting Veeam flaw CVE-2023-27532 with an aim to enable xp cmdshell on the backup server and create a rogue user account named "VeeamBkp," alongside conducting network discovery, enumeration, and credential harvesting activities using tools like NetScan, AdFind, and NitSoft using the newly created account.
"This exploitation potentially involved an attack originating from the VeeamHax folder on the file server against the vulnerable version of Veeam Backup & Replication software installed on the backup server," Zi Wei hypothesized.
The disclosure comes as Cisco Talos revealed that most ransomware gangs prioritize establishing initial access using security flaws in public-facing applications, phishing attachments, or breaching valid accounts, and circumventing defenses in their attack chains.
"Over the past year, we have witnessed major shifts in the ransomware space with the emergence of multiple new ransomware groups, each exhibiting unique goals, operational structures and victimology," Talos said.
News URL
https://thehackernews.com/2024/07/new-ransomware-group-exploiting-veeam.html
Related news
Related Vulnerability
| DATE | CVE | VULNERABILITY TITLE | RISK |
|---|---|---|---|
| 2023-03-10 | CVE-2023-27532 | Missing Authentication for Critical Function vulnerability in Veeam Backup & Replication Vulnerability in Veeam Backup & Replication component allows encrypted credentials stored in the configuration database to be obtained. | 7.5 |