Security News > 2023 > May > Researchers Uncover New Exploit for PaperCut Vulnerability That Can Bypass Detection
Cybersecurity researchers have found a way to exploit a recently disclosed critical flaw in PaperCut servers in a manner that bypasses all current detections.
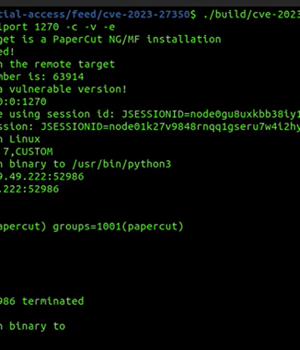
Tracked as CVE-2023-27350, the issue affects PaperCut MF and NG installations that could be exploited by an unauthenticated attacker to execute arbitrary code with SYSTEM privileges.
Now, VulnCheck has published a proof-of-concept exploit that sidesteps existing detection signatures by leveraging the fact that "PaperCut NG and MF offer multiple paths to code execution."
It's worth noting that public exploits for the flaw use the PaperCut printer scripting interface to either execute Windows commands or drop a malicious Java archive file.
The PoC exploit devised by VulnCheck banks on the auth program set as "/usr/sbin/python3" for Linux and "C:WindowsSystem32ftp.exe" for Windows.
"An administrative user attacking PaperCut NG and MF can follow multiple paths to arbitrary code execution," VulnCheck pointed out.
News URL
https://thehackernews.com/2023/05/researchers-uncover-new-exploit-for.html
Related Vulnerability
| DATE | CVE | VULNERABILITY TITLE | RISK |
|---|---|---|---|
| 2023-04-20 | CVE-2023-27350 | Unspecified vulnerability in Papercut MF and Papercut NG This vulnerability allows remote attackers to bypass authentication on affected installations of PaperCut NG 22.0.5 (Build 63914). | 9.8 |