Security News > 2022 > November > Worok Hackers Abuse Dropbox API to Exfiltrate Data via Backdoor Hidden in Images
A recently discovered cyber espionage group dubbed Worok has been found hiding malware in seemingly innocuous image files, corroborating a crucial link in the threat actor's infection chain.
Czech cybersecurity firm Avast said the purpose of the PNG files is to conceal a payload that's used to facilitate information theft.
"What is noteworthy is data collection from victims' machines using DropBox repository, as well as attackers using DropBox API for communication with the final stage," the company said.
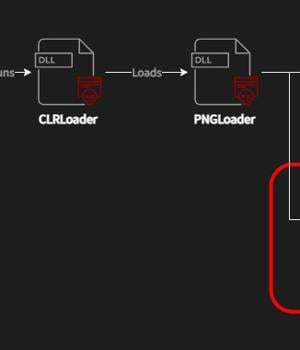
PNGLoad, which is launched by CLRLoad, is said to come in two variants, each responsible for decoding the malicious code within the image to launch either a PowerShell script or a.NET C#-based payload. The PowerShell script has continued to be elusive, although Avast noted it was able to flag a few PNG files belonging to the second category that dispensed a steganographically embedded C# malware.
This new malware, dubbed DropBoxControl, is an information-stealing implant that uses a Dropbox account for command-and-control, enabling the threat actor to upload and download files to specific folders as well as run commands present in a certain file.
Some of the notable commands include the ability to execute arbitrary executables, download and upload data, delete and rename files, capture file information, sniff network communications, and exfiltrate system metadata.
News URL
https://thehackernews.com/2022/11/worok-hackers-abuse-dropbox-api-to.html