Security News > 2022 > November > Researchers Disclose Details of Critical 'CosMiss' RCE Flaw Affecting Azure Cosmos DB
Microsoft on Tuesday said it addressed an authentication bypass vulnerability in Jupyter Notebooks for Azure Cosmos DB that enabled full read and write access.
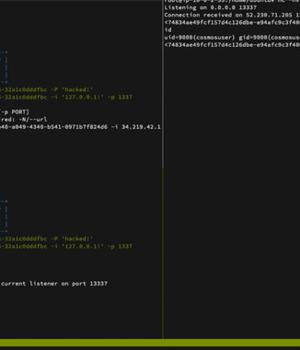
The tech giant said the problem was introduced on August 12, 2022, and rectified worldwide on October 6, 2022, two days after responsible disclosure from Orca Security, which dubbed the flaw CosMiss. "In short, if an attacker had knowledge of a Notebook's 'forwardingId,' which is the UUID of the Notebook Workspace, they would have had full permissions on the Notebook without having to authenticate, including read and write access, and the ability to modify the file system of the container running the notebook," researchers Lidor Ben Shitrit and Roee Sagi said.
This container modification could ultimately pave the way for obtaining remote code execution in the Notebook container by overwriting a Python file associated with the Cosmos DB Explorer to spawn a reverse shell.
Successful exploitation of the flaw requires that the adversary is in possession of the unique 128-bit forwardingId and that it's put to use within a one-hour window, after which the temporary Notebook is automatically deleted.
"The vulnerability, even with knowledge of the forwardingId, did not give the ability to execute notebooks, automatically save notebooks in the victim's connected GitHub repository, or access to data in the Azure Cosmos DB account," Redmond said.
"Customers not using Jupyter Notebooks were not susceptible to this vulnerability," it further said.
News URL
https://thehackernews.com/2022/11/researchers-disclose-details-of.html
Related news
- Researchers Uncover 46 Critical Flaws in Solar Power Systems From Sungrow, Growatt, and SMA (source)
- OpenAI now pays researchers $100,000 for critical vulnerabilities (source)
- Gladinet’s Triofox and CentreStack Under Active Exploitation via Critical RCE Vulnerability (source)
- Critical Erlang/OTP SSH pre-auth RCE is 'Surprisingly Easy' to exploit, patch now (source)
- Critical Erlang/OTP SSH RCE bug now has public exploits, patch now (source)
- Critical Commvault RCE vulnerability fixed, PoC available (CVE-2025-34028) (source)
- Critical Langflow RCE flaw exploited to hack AI app servers (source)
- SysAid Patches 4 Critical Flaws Enabling Pre-Auth RCE in On-Premise Version (source)
- Unpatched critical bugs in Versa Concerto lead to auth bypass, RCE (source)